hi,我是蛋挞,一个初出茅庐的后端开发,希望可以和大家共同努力、共同进步!
开启掘金成长之旅!这是我参与「掘金日新计划 · 4 月更文挑战」的第 8 天,点击查看活动详情
- 起始标记->保护你的数据(3讲):「56 | 集群身份认证与用户鉴权」
- 结尾标记->保护你的数据(3讲):「58 | 集群与外部间的安全通信」
集群身份认证与用户鉴权
5700万用户数据泄漏
就在近日,有外媒报道显示: ElascSearch服务器(一种用于支持搜索功能的技术)在没有密码的开放状态下泄露了将近5700万 美国民众的个人信息。 据称,该漏洞最初是由网络安全公司Hacken的网络风险研究主管Bob Diachenko发现,他表示ElasticSearch服务器共泄漏了超过73GB的数据,并且几个数据库被缓存在服务器的内存中。而其中一个数据库就包含有美国公民的个人信息共计56,934,021份。 Bob Diachenko表示,被泄露的个人数据主要包含有姓名、电子邮件地址、家庭地址、州、邮政编码、电话号码、IP地址等个人信息。 但本次数据泄露远不止这么简单,根据Diachenko表示,泄密的ElasticSearch服务器中还包含有一个名为“黄页”的缓存数据库里面包含有25,917,820条记录,而这些记录似乎为商业条目。和第一个数据库相比包含有更多的信息,其中包括有姓名、公司详细信息、邮政编码、承运人路线、纬度/经度坐标、人口普查区、电话号码、web地址、电子部件地址、员工人数、收入编号、NAICS代码、SIC代码,以及其他一些字段。
1.08 亿条投注信息泄漏
据外媒报道,美国一家网上赌场集团已经泄露了超过1.08亿笔投注的信息,其中包括有关客户个人信息,存款和取款等详细信息。 对此,安全研究员表示,这些数据是从 Elasticsearch 服务器泄露出来的,并且不需要密码就可获得这些信息。 Elasticsearch 是一个搜索引擎,该引警多是应用在企业内部用来处理敏感信息,一般这些信息不会泄露到网上。 安全研究员 Justin Paine 在上周就发现这个没有安全保护和身份验证的 Elasticsearch 实例,并确认了这是在线投注有关的信息。尽管服务器只有一个,但该 Elasticsearch 处理的信息大且来自多个网站,可以判断信息出处是一家运营多个博彩门户的大公司。 泄漏数据中,好消息是银行卡信息被部分加密、没有公开完整的财务细节。坏消息则是近期赢得大第金钱的玩家可能会有麻烦了,他们的姓名、家庭住址和电话号码已遭泄露一这些玩家可能会被发现该数据库的人敲诈和勤索
原因分析
- Elasticsearch 在默认安装后,不提供任何形式的安全防护
- 错误的配置信息导致公网可以访问 ES 集群
- 在 elasticsearch.yml 文件中,server.host 被错误的配置为 0.0.0.0
数据安全性的基本需求
- 身份认证
- 鉴定用户是否合法
- 用户鉴权
- 指定那个用户可以访问哪个索引
- 传输加密
- 日志审计
些免费的方案
- 设置 Nginx 反向代理
- 安装免费的 Security 插件
- Search Guard - search-guard.com/
- ReadOnly REST - github.com/sscarduzio/…
- X-Pack 的 Basic 版
- 从ES 6.8 & ES 7.0开始,Security 纳入 x-pack 的 Basic 版本中,免费使用一些基本的功能
- www.elastic.co/what-is/ela…
Authentication -身份认证
- 认证体系的几种类型
- 提供用户名和密码
- 提供秘钥或 Kerberos 票据
- Realms: X-Pack 中的认证服务
- 内置 Realms (免费)
- File /Native (用户名密码保存在 Elasticsearch)
- 外部 Realms (收费)
- LDAP TActive Directory IPKISAMLKerberos
- 内置 Realms (免费)
RBAC- 用户鉴权
- 什么是 RBAC: Role Based Access Control,定义一个角色,并分配一组权限。权限包括索引级,字段级,集群级的不同的操作。然后通过将角色分配给用户,使得用户拥有这些权限
- User: The authenticated User
- Role: A named set of permissions
- Permission - A set of one or more privileges against a secured resource
- Privilege - A named group of 1 or more actions that user may execute against a secured resource
创建内置的用户和角色
- 内置的角色与用户 | 用户 | 角色 | | --- | --- | | elastic | Supper User | | kibana | The user that is used by Kibana to connect and communicate withElasticsearch. | | logstash_system | The user that is used by Logstash when storing monitoring informationin Elasticsearch. | | beats_system | The user that the different Beats use when storing monitoringinformation in Elasticsearch. | | apm_system | The user that the APM server uses when storing monitoring informationin Elasticsearch. | | Remote_monitoring_user | The user that is used by Metricbeat when collecting and storingmonitoring information in Elasticsearch. |
使用 Security API创建用户
| User |
- Create user
- Update user
- Delete user
- Enable / disable users
- Get users
- Change password | | --- | --- | | Role |
- Create Role
- Update Role
- Delete Role
- Get roles |
开启并配置 X-Pack 的认证与鉴权
- 修改配置文件,打开认证与授权
- bin/elasticsearch -E nodename=node0 -E cluster.name=geektime -E path.data=node0_data - E http.port=9200 -E xpack.security.enabled=truel
- 创建默认的用户和分组
- bin/elasticsearch-password interactive
- 当集群开启身份认证之后,配置 Kibana
- Demo
- 创建一个 Bole 配置为对其个索引只读权限/创建一个用户,把用户加入 Bole
CodeDemo
#启动单节点
bin/elasticsearch -E node.name=node0 -E cluster.name=geektime -E path.data=node0_data -E http.port=9200 -E xpack.security.enabled=true
#使用Curl访问ES,或者浏览器访问 “localhost:9200/_cat/nodes?pretty”。返回401错误
curl 'localhost:9200/_cat/nodes?pretty'
#运行密码设定的命令,设置ES内置用户及其初始密码。
bin/elasticsearch-setup-passwords interactive
curl -u elastic 'localhost:9200/_cat/nodes?pretty'
# 修改 kibana.yml
elasticsearch.username: "kibana"
elasticsearch.password: "changeme"
#启动。使用用户名,elastic,密码elastic
./bin/kibana
POST orders/_bulk
{"index":{}}
{"product" : "1","price" : 18,"payment" : "master","card" : "9876543210123456","name" : "jack"}
{"index":{}}
{"product" : "2","price" : 99,"payment" : "visa","card" : "1234567890123456","name" : "bob"}
#create a new role named read_only_orders, that satisfies the following criteria:
#The role has no cluster privileges
#The role only has access to indices that match the pattern sales_record
#The index privileges are read, and view_index_metadata
#create sales_user that satisfies the following criteria:
# Use your own email address
# Assign the user to two roles: read_only_orders and kibana_user
#验证读权限,可以执行
POST orders/_search
{}
#验证写权限,报错
POST orders/_bulk
{"index":{}}
{"product" : "1","price" : 18,"payment" : "master","card" : "9876543210123456","name" : "jack"}
{"index":{}}
{"product" : "2","price" : 99,"payment" : "visa","card" : "1234567890123456","name" : "bob"}
相关阅读
集群身份认证与用户鉴权
- 如何为集群启用X-Pack Security
- 如何为内置用户设置密码
- 设置 Kibana与ElasticSearch通信鉴权
- 使用安全API创建对特定索引具有有限访问权限的用户
This tutorial involves a single node cluster, but if you had multiple nodes, you would enable Elasticsearch security features on every node in the cluster and configure Transport Layer Security (TLS) for internode-communication, which is beyond the scope of this tutorial. By enabling single-node discovery, we are postponing the configuration of TLS. For example, add the following setting: discovery.type: single-node
本节知识总结
介绍了安全对于数据的重要性,演示了如何在Elasticsearch中通过X-Pack的安全功能保护数据。
集群内部安全通信
为什么要加密通讯
- 加密数据- 避免数据抓包,敏感信息泄漏
- 验证身份 - 避免 mpostor Node
- Data / Cluster State
为节点创建证书
- TLS
- TLS 协议要求 Trusted Certificate Authority (CA) 签发的 X509的证书
- 证书认证的不同级别
- Certificate 一节点加入需要使用相同 CA 签发的证书
- Full Verification - 节点加入集群需要相同 CA 签发的证书,还需要验证 Host name 或IP 地址
- No Verification - 任何节点都可以加入,开发环境中用于诊断目的
生成节点证书
- bin/elasticsearch-certutil ca
- bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12
- www.elastic.co/guide/en/el…
配置节点间通讯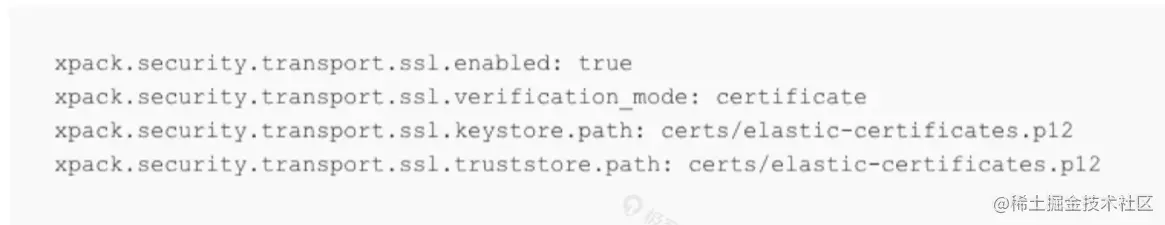
CodeDemo
# 生成证书
# 为您的Elasticearch集群创建一个证书颁发机构。例如,使用elasticsearch-certutil ca命令:
bin/elasticsearch-certutil ca
#为群集中的每个节点生成证书和私钥。例如,使用elasticsearch-certutil cert 命令:
bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12
#将证书拷贝到 config/certs目录下
elastic-certificates.p12
bin/elasticsearch -E node.name=node0 -E cluster.name=geektime -E path.data=node0_data -E http.port=9200 -E xpack.security.enabled=true -E xpack.security.transport.ssl.enabled=true -E xpack.security.transport.ssl.verification_mode=certificate -E xpack.security.transport.ssl.keystore.path=certs/elastic-certificates.p12 -E xpack.security.transport.ssl.truststore.path=certs/elastic-certificates.p12
bin/elasticsearch -E node.name=node1 -E cluster.name=geektime -E path.data=node1_data -E http.port=9201 -E xpack.security.enabled=true -E xpack.security.transport.ssl.enabled=true -E xpack.security.transport.ssl.verification_mode=certificate -E xpack.security.transport.ssl.keystore.path=certs/elastic-certificates.p12 -E xpack.security.transport.ssl.truststore.path=certs/elastic-certificates.p12
#不提供证书的节点,无法加入
bin/elasticsearch -E node.name=node2 -E cluster.name=geektime -E path.data=node2_data -E http.port=9202 -E xpack.security.enabled=true -E xpack.security.transport.ssl.enabled=true -E xpack.security.transport.ssl.verification_mode=certificate
## elasticsearch.yml 配置
#xpack.security.transport.ssl.enabled: true
#xpack.security.transport.ssl.verification_mode: certificate
#xpack.security.transport.ssl.keystore.path: certs/elastic-certificates.p12
#xpack.security.transport.ssl.truststore.path: certs/elastic-certificates.p12
相关阅读
集群与外部间的安全通信
为什么需要HTTPS
配置 Elasticsearch for HTTPS
配置 Kibana 连接 ES HTTPS
You need to update the configuration file kibanayml to setup encrypted communications. Youwill need to configure two settings:
- Change the Elasticsearch hosts to use the HTTPS protocol
2 Provide the path to the CA certificate in order to authenticate Kibana
For example:
配置使用HTTPS访问 Kibana
This is a two-step process:
- The first step is to generate a server certificate for Kibana the same way that you created anode certificate for every node of your Elasticsearch cluster. Except this time it requirescertificates and keys in PEM format instead of PKCS#12. Once again you will use the certutiltool from Elasticsearch to generate the node certificates:
The PEM output will generate two files, one for the private keyand another one for thecertificate.
- You need to update the configuration file of your Kibana to enable SSL between Kibana andthe browser, and add the path to the different files that you generated:
CodeDemo
xpack.security.http.ssl.enabled: true
xpack.security.http.ssl.keystore.path: certs/elastic-certificates.p12
xpack.security.http.ssl.truststore.path: certs/elastic-certificates.p12
# ES 启用 https
bin/elasticsearch -E node.name=node0 -E cluster.name=geektime -E path.data=node0_data -E http.port=9200 -E xpack.security.enabled=true -E xpack.security.transport.ssl.enabled=true -E xpack.security.transport.ssl.verification_mode=certificate -E xpack.security.transport.ssl.keystore.path=certs/elastic-certificates.p12 -E xpack.security.http.ssl.enabled=true -E xpack.security.http.ssl.keystore.path=certs/elastic-certificates.p12 -E xpack.security.http.ssl.truststore.path=certs/elastic-certificates.p12
#Kibana 连接 ES https
# 为kibana生成pem
openssl pkcs12 -in elastic-certificates.p12 -cacerts -nokeys -out elastic-ca.pem
elasticsearch.hosts: ["https://localhost:9200"]
elasticsearch.ssl.certificateAuthorities: [ "/Users/yiruan/geektime/kibana-7.1.0/config/certs/elastic-ca.pem" ]
elasticsearch.ssl.verificationMode: certificate
# 为 Kibna 配置 HTTPS
# 生成后解压,包含了instance.crt 和 instance.key
bin/elasticsearch-certutil ca --pem
server.ssl.enabled: true
server.ssl.certificate: config/certs/instance.crt
server.ssl.key: config/certs/instance.key
相关阅读
本节知识总结
演示了如何设置Elasticsearch和Kinbana的https的支持,通过设置https的支持,我们保存在Elasticsearch中的数据才能得到更好的保护。
此文章为4月Day8学习笔记,内容来源于极客时间《Elasticsearch 核心技术与实战》