- 发现问题
- 在一次后端更新以后发现 苹果推送出现问题
- 后端人员查了半天以后表示..真的什么都没改,我也不知道为什么!!!
- 扒日志找到了java抛出的异常
Causing: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
! at java.base/sun.security.validator.PKIXValidator.doBuild(Unknown Source)
! at java.base/sun.security.validator.PKIXValidator.engineValidate(Unknown Source)
! at java.base/sun.security.validator.Validator.validate(Unknown Source)
! at java.base/sun.security.ssl.X509TrustManagerImpl.validate(Unknown Source)
! at java.base/sun.security.ssl.X509TrustManagerImpl.checkTrusted(Unknown Source)
! at java.base/sun.security.ssl.X509TrustManagerImpl.checkServerTrusted(Unknown Source)
! at io.netty.handler.ssl.ReferenceCountedOpenSslClientContext$ExtendedTrustManagerVerifyCallback.verify(ReferenceCountedOpenSslClientContext.java:242)
! at io.netty.handler.ssl.ReferenceCountedOpenSslContext$AbstractCertificateVerifier.verify(ReferenceCountedOpenSslContext.java:655)
! ... 27 common frames omitted
! Causing: javax.net.ssl.SSLHandshakeException: General OpenSslEngine problem
! at io.netty.handler.ssl.ReferenceCountedOpenSslContext$AbstractCertificateVerifier.verify(ReferenceCountedOpenSslContext.java:659)
! at io.netty.internal.tcnative.SSL.readFromSSL(Native Method)
! at io.netty.handler.ssl.ReferenceCountedOpenSslEngine.readPlaintextData(ReferenceCountedOpenSslEngine.java:575)
! at io.netty.handler.ssl.ReferenceCountedOpenSslEngine.unwrap(ReferenceCountedOpenSslEngine.java:1124)
! at io.netty.handler.ssl.ReferenceCountedOpenSslEngine.unwrap(ReferenceCountedOpenSslEngine.java:1236)
! at io.netty.handler.ssl.ReferenceCountedOpenSslEngine.unwrap(ReferenceCountedOpenSslEngine.java:1279)
! at io.netty.handler.ssl.SslHandler$SslEngineType$1.unwrap(SslHandler.java:217)
! at io.netty.handler.ssl.SslHandler.unwrap(SslHandler.java:1301)
! at io.netty.handler.ssl.SslHandler.decodeNonJdkCompatible(SslHandler.java:1215)
! ... 19 common frames omitted
! Causing: java.util.concurrent.ExecutionException: javax.net.ssl.SSLHandshakeException: General OpenSslEngine problem
! at io.netty.util.concurrent.AbstractFuture.get(AbstractFuture.java:41)
! at io.netty.util.concurrent.DefaultPromise.notifyListener0(DefaultPromise.java:511)
! at io.netty.util.concurrent.DefaultPromise.notifyListeners0(DefaultPromise.java:504)
! at io.netty.util.concurrent.DefaultPromise.notifyListenersNow(DefaultPromise.java:483)
- 猛的一看,不就是https交互时握手的证书问题嘛
- 然后各种谷歌百度,这个异常应该就是这个问题才是
-
然后用chrome打开苹果推送域名api.push.apple.com,发现证书是正常的,至少谷歌认为是正常的.想想也是苹果这么大公司,不至于证书都有问题
-
那么问题来了,继续复盘,我们做了什么导致了这个问题,查了半天结果是什么都没做.真的冤枉,啥都没做啊!把修改回滚回去还是出这问题,这就很尴尬了
-
找了半天,终于在我的不懈努力下(其实就是疯狂想到底什么地方可能跟以前不一样,基本都是瞎想)...,终于想到一种可能
- 我们的后端应用是打包成镜像的,基础镜像是
openjdk:11-jre,是不是基础镜像变了的原因(我非常怀疑这是我的瞎想,毕竟是官方的镜像,出问题的概率应该不高)
- 做了一下实验,在更新前基础镜像
openjdk:11-jre链接指的是openjdk:11.0.6-jre,更新后基础镜像链接指的是openjdk:11.0.8-jre.
- 然后我们直接把基础镜像从
openjdk:11-jre改成openjdk:11.0.6-jre - 结果,居然正常了...所以真的是基础镜像的问题
- 调查,基础镜像到底发生了什么事情导致的这个问题.通过一翻查找(过程省略)找到了github的这个issue,这个issue已经说明了很多的原因
https://github.com/docker-library/openjdk/issues/414
- issue主要的部分是有个人提问,我代码出了异常,检查了一下是根证书神奇的少了几个,这是咋回事,是不是你们官方的人弄没的
- 然后官方的人解释-这不关我们的事情,我们openjdk只负责把jdk丢进镜像里,具体的根证书其实是我们的上游镜像debian-buster搞的(这里解释一下,debian是linux的一比较古老并且由社区维护的一个发行版,并且这个社区维护的都是开源的项目,所以debian默认的源都是开源软件,这个发行版久负盛名.著名的ubuntu就是基于debian发行的.而debian-buster就是debian第10个主要版本,是debian目前最新的的版本)
- 然后同时给出了debian发行版一个更新的日志链接
- 这个debian发行版更新日志链接在这里
https://tracker.debian.org/news/1150838/accepted-ca-certificates-20200601deb10u1-source-into-proposed-updates-stable-new-proposed-updates/
- 更新日志指出将根证书更新为
Mozilla的根证书列表2.4版本,移除了一点点处于黑名单的证书,例如塞克铁门的一个根证书 - 然后在更新日志里还链接了提到这个问题的几个bugreport,类似与issue一样
- 然后我找了一下,我在其中一个bugreport找到了这次更新的证书的列表,bugreport的地址是
https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=955038
- 这些bugreport表示,有些根证书已经过期了,有些根证书被黑名单了,被Mozilla移除了,你咋不跟上呢
- 管理员觉得,嗯你说的对,然后还列出了具体改了啥,内容在下面
* debian/control:
Set Standards-Version: 4.5.0.2
Set Build-Depends: debhelper-compat (= 13)
* debian/copyright:
Replace tabs in license text
* mozilla/{certdata.txt,nssckbi.h}:
Update Mozilla certificate authority bundle to version 2.40.
Closes: #956411, #955038
* mozilla/blacklist.txt
Add distrusted Symantec CA list to blacklist for explicit removal.
Closes: #911289
Blacklist expired root certificate, "AddTrust External Root"
Closes: #961907
The following certificate authorities were added (+):
+ "Certigna Root CA"
+ "emSign ECC Root CA - C3"
+ "emSign ECC Root CA - G3"
+ "emSign Root CA - C1"
+ "emSign Root CA - G1"
+ "Entrust Root Certification Authority - G4"
+ "GTS Root R1"
+ "GTS Root R2"
+ "GTS Root R3"
+ "GTS Root R4"
+ "Hongkong Post Root CA 3"
+ "UCA Extended Validation Root"
+ "UCA Global G2 Root"
The following certificate authorities were removed (-):
- "AddTrust External Root"
- "Certinomis - Root CA"
- "Certplus Class 2 Primary CA"
- "Deutsche Telekom Root CA 2"
- "GeoTrust Global CA"
- "GeoTrust Primary Certification Authority"
- "GeoTrust Primary Certification Authority - G2"
- "GeoTrust Primary Certification Authority - G3"
- "GeoTrust Universal CA"
- "thawte Primary Root CA"
- "thawte Primary Root CA - G2"
- "thawte Primary Root CA - G3"
- "VeriSign Class 3 Public Primary Certification Authority - G4"
- "VeriSign Class 3 Public Primary Certification Authority - G5"
- "VeriSign Universal Root Certification Authority"
Checksums-Sha1:
a50340689426d06821d0200f76b674f81c27e703 1582 ca-certificates_20200601.dsc
f17235bc9c3aec538065a655681815c242a6d7d5 245668 ca-certificates_20200601.tar.xz
Checksums-Sha256:
4c18f8be89824bc7e4c51895e513b0d8b748ea84e8190571aa4126ad9dcdd1fe 1582 ca-certificates_20200601.dsc
43766d5a436519503dfd65ab83488ae33ab4d4ca3d0993797b58c92eb9ed4e63 245668 ca-certificates_20200601.tar.xz
Files:
47c286787c4b1c5881721370eec53369 1582 misc optional ca-certificates_20200601.dsc
9b37bd1bc002d9f041c0a811667cb65a 245668 misc optional ca-certificates_20200601.tar.xz
- 我们可以看到
The following certificate authorities were removed(以下的证书会被移除)列表里面有个证书是GeoTrust Global CA
- 我们直接用chrome访问
api.push.apple.com,然后打开证书列表
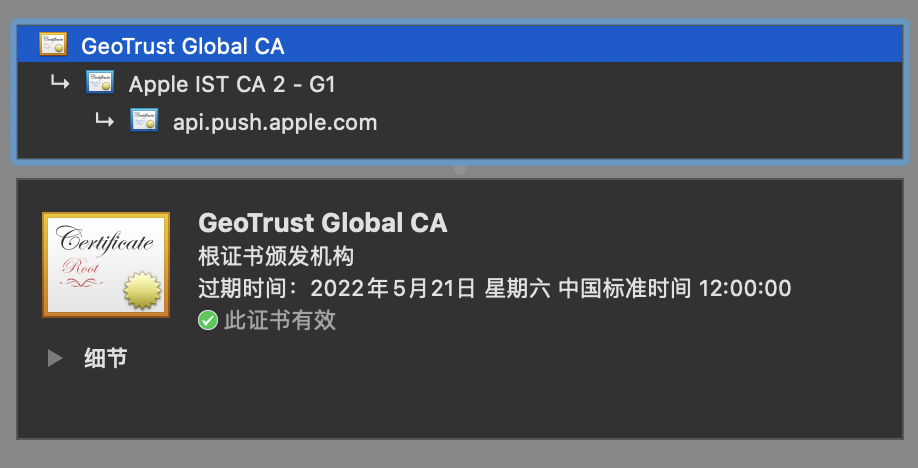
看到最上面的根证书,这,这不就是被移除的GeoTrust Global CA嘛!这下真相大白了.
- 好消息是,我们用的
letsencrypt的证书好像没啥问题哈哈