上篇文章描述了,nginx-ingress控制器,接下来简单讲讲istio-ingressgateway。
传送门 juejin.cn/post/684490…
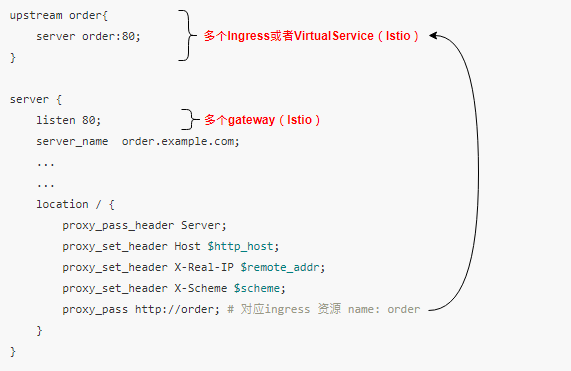
如果看懂上图,基本不用往下看了
在istio 0.8版本之前使用的是上一篇中的ingress来描述服务访问入口的,因为ingress的七层限制,istio版本V1alpha3流量规则中引入了gateway资源对象,只定义接入点。那么和nginx-ingress有什么区别呢?
其实就是主要做了两件事:
- 新增了gateway资源,这个gateway资源是什么玩意呢?也是用yaml描述文件管理的,nginx-ingress只暴漏了两个端口
80和443,现在istio-ingressgateway通过gateway可以暴漏多个端口了。gateway中配置的端口就为istio-ingressgateway这个pod暴漏的端口,就是对应的service的targetPort。 - 把nginx换成了envoy
1、官方demo中的istio-ingressgateway的deployment和service
deployment
apiVersion: apps/v1
kind: Deployment
metadata:
name: istio-ingressgateway
namespace: istio-system
labels:
chart: gateways
heritage: Tiller
release: istio
app: istio-ingressgateway
istio: ingressgateway
spec:
replicas: 1
selector:
matchLabels:
app: istio-ingressgateway
istio: ingressgateway
strategy:
rollingUpdate:
maxSurge: 100%
maxUnavailable: 25%
template:
metadata:
labels:
chart: gateways
heritage: Tiller
release: istio
app: istio-ingressgateway
istio: ingressgateway
annotations:
sidecar.istio.io/inject: "false"
spec:
serviceAccountName: istio-ingressgateway-service-account
containers:
- name: istio-proxy
image: "docker.io/istio/proxyv2:1.3.0"
imagePullPolicy: IfNotPresent
ports:
- containerPort: 15020
- containerPort: 80
- containerPort: 443
- containerPort: 31400
- containerPort: 15029
- containerPort: 15030
- containerPort: 15031
- containerPort: 15032
- containerPort: 15443
- containerPort: 15090
protocol: TCP
name: http-envoy-prom
args:
- proxy
- router
- --domain
- $(POD_NAMESPACE).svc.cluster.local
- --log_output_level=default:info
- --drainDuration
- '45s' #drainDuration
- --parentShutdownDuration
- '1m0s' #parentShutdownDuration
- --connectTimeout
- '10s' #connectTimeout
- --serviceCluster
- istio-ingressgateway
- --zipkinAddress
- zipkin:9411
- --proxyAdminPort
- "15000"
- --statusPort
- "15020"
- --controlPlaneAuthPolicy
- NONE
- --discoveryAddress
- istio-pilot:15010
readinessProbe:
failureThreshold: 30
httpGet:
path: /healthz/ready
port: 15020
scheme: HTTP
initialDelaySeconds: 1
periodSeconds: 2
successThreshold: 1
timeoutSeconds: 1
resources:
limits:
cpu: 2000m
memory: 1024Mi
requests:
cpu: 10m
memory: 40Mi
env:
- name: NODE_NAME
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: spec.nodeName
- name: POD_NAME
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: metadata.namespace
- name: INSTANCE_IP
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: status.podIP
- name: HOST_IP
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: status.hostIP
- name: SERVICE_ACCOUNT
valueFrom:
fieldRef:
fieldPath: spec.serviceAccountName
- name: ISTIO_META_POD_NAME
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: metadata.name
- name: ISTIO_META_CONFIG_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: SDS_ENABLED
value: "false"
- name: ISTIO_META_WORKLOAD_NAME
value: istio-ingressgateway
- name: ISTIO_META_OWNER
value: kubernetes://api/apps/v1/namespaces/istio-system/deployments/istio-ingressgateway
- name: ISTIO_META_ROUTER_MODE
value: sni-dnat
volumeMounts:
- name: istio-certs
mountPath: /etc/certs
readOnly: true
- name: ingressgateway-certs
mountPath: "/etc/istio/ingressgateway-certs"
readOnly: true
- name: ingressgateway-ca-certs
mountPath: "/etc/istio/ingressgateway-ca-certs"
readOnly: true
volumes:
- name: istio-certs
secret:
secretName: istio.istio-ingressgateway-service-account
optional: true
- name: ingressgateway-certs
secret:
secretName: "istio-ingressgateway-certs"
optional: true
- name: ingressgateway-ca-certs
secret:
secretName: "istio-ingressgateway-ca-certs"
optional: true
affinity:
nodeAffinity:
requiredDuringSchedulingIgnoredDuringExecution:
nodeSelectorTerms:
- matchExpressions:
- key: beta.kubernetes.io/arch
operator: In
values:
- "amd64"
- "ppc64le"
- "s390x"
preferredDuringSchedulingIgnoredDuringExecution:
- weight: 2
preference:
matchExpressions:
- key: beta.kubernetes.io/arch
operator: In
values:
- "amd64"
- weight: 2
preference:
matchExpressions:
- key: beta.kubernetes.io/arch
operator: In
values:
- "ppc64le"
- weight: 2
preference:
matchExpressions:
- key: beta.kubernetes.io/arch
operator: In
values:
- "s390x"
service
apiVersion: v1
kind: Service
metadata:
name: istio-ingressgateway
namespace: istio-system
annotations:
labels:
chart: gateways
heritage: Tiller
release: istio
app: istio-ingressgateway
istio: ingressgateway
spec:
type: LoadBalancer
selector:
release: istio
app: istio-ingressgateway
istio: ingressgateway
ports:
-
name: status-port
port: 15020
targetPort: 15020
-
name: http2
nodePort: 31380
port: 80
targetPort: 80 # 官方已经帮我们映射好了80端口
-
name: https
nodePort: 31390
port: 443
-
name: tcp
nodePort: 31400
port: 31400
-
name: https-kiali
port: 15029
targetPort: 15029
-
name: https-prometheus
port: 15030
targetPort: 15030
-
name: https-grafana
port: 15031
targetPort: 15031
-
name: https-tracing
port: 15032
targetPort: 15032
-
name: tls
port: 15443
targetPort: 15443
2、自定义service
首先apply gateway、VirtualService、DestinationRule
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: dk-shop
namespace: dk-shop
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 80 # 比如nginx监听的80端口,就是istio-ingressgateway pod暴漏的端口,对应的是service的targetPort,请看下边的service
name: http
protocol: HTTP
hosts:
- "*"
- user.thanhoo.com
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: user
namespace: dk-shop
spec:
hosts:
- "user.thanhoo.com"
gateways:
- dk-shop
http:
- route:
- destination:
host: user
port:
number: 80
subset: v1
---
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: user
namespace: dk-shop
spec:
host: user
trafficPolicy:
loadBalancer:
simple: RANDOM
subsets:
- name: v1
labels:
version: v1.0
- name: v2
labels:
version: v2.0
自定义service
apiVersion: v1
kind: Service
metadata:
name: dk-shop-gateway
namespace: istio-system # 注意命名空间
annotations:
labels:
app: dk-shop-gateway
spec:
type: NodePort
selector:
app: istio-ingressgateway
ports:
- name: http2
nodePort: 30001 # 其实和官方就是端口不一样,labe简化一些
port: 80
targetPort: 80
官方的service执行
curl -HHost:user.thanhoo.com http://127.0.0.1:31380
HTTP/1.1 200 OK
content-type: application/json; charset=utf-8
server: istio-envoy
content-length: 5
x-envoy-upstream-service-time: 0
date: Sat, 05 Oct 2019 11:45:34 GMT
自定义的service执行
curl -i -HHost:user.thanhoo.com http://127.0.0.1:30001
HTTP/1.1 200 OK
content-type: application/json; charset=utf-8
server: istio-envoy
content-length: 5
x-envoy-upstream-service-time: 0
date: Sat, 05 Oct 2019 11:46:30 GMT