声明:掘金用户在稀土掘金(juejin.cn)上发表的内容仅表明原始文章作者个人的立场和观点,并不代表稀土掘金的立场或观点。
The 360 browser is a popular browser on both the PC and mobile platforms in the Chinese market. It is known for its security, and has a total download number of more than 460 million on the 360 market, Tencent market and Wandoujia.com combined.
360浏览器是中国PC和手机平台市场上一款流行的浏览器。它以保护用户设备安全而出名,在360、腾讯和豌豆荚市场共计超过4亿6千万次下载。
24 hours ago, a new vulnerability of the 360 browser was posted on Wooyun.org [1] (a popular vulnerability disclosure platform in China). After careful analysis of the 360 safe browser (com.qihoo.expressbrowser), another critical “wormhole” vulnerability was found.
24小时前,乌云漏洞报告平台首先发布了在360浏览器中发现的一个新型漏洞。经过对360安全浏览器(com.qihoo.expressbrowser)的详细分析,另一个严重的“虫洞”漏洞浮现。
Like the “Wormhole” and “DimensionDoor”, the vulnerability is triggered on a customized HTTP service. We noticed that HTTP service will not be shutdown even after the app is patched. To stop this service, users need to manually disable it in the system settings, or reboot the phone.
类似“虫洞(Wormhole)”与“异次元之门(DimensionDoor)”,此漏洞可通过定制的HPPT服务被触发。我们注意到,即使为APP打上补丁,HTTP服务也不会被关闭。若要终止服务,用户只能在系统设置中手动暂停服务或重新启动移动设备。
Qihoo pushed the update 6.9.9.71 beta on Nov 23 to address this bug. According to our tests, the previous versions before Nov 23, such as 6.9.9.70 beta, are vulnerable. If you are using the 360 browser, and haven’t update it after Nov 23, please make sure to update it to 6.9.9.71 beta or newer,then restart your phone.
为了修补这个漏洞,奇虎在11月23日更新发布了6.9.9.71测试版。根据我们的检测,所有在11月23日之前发布的,例如6.9.9.70测试版,都是存在漏洞、易受攻击的版本。如果你正在使用360浏览器,并且没有将其更新至11月23日之后的版本,请确保升级至6.9.9.71测试版及更新的版本,然后重新启动你的手机。
This vulnerability could lead to remote code execution on any Android phone with a 360 browser installed. Keywords: Remote, Silence, Flexible.
这个漏洞可导致在任意安装了360浏览器的安卓手机上实现远程代码执行。
关键词:远程,静默,灵活。
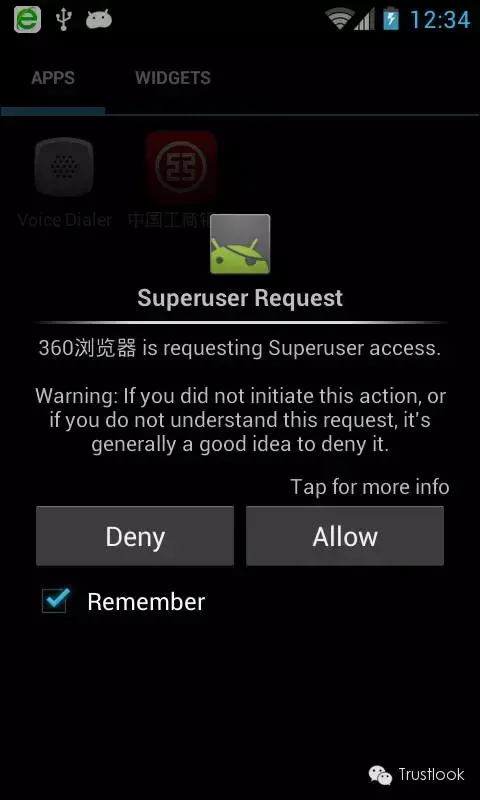
For rooted phones: the attacker can do pretty much everything, such as install APKs from the Internet in the background, access emails & SMS, and monitor the camera and microphone.It is more flexible than the “DimensionDoor”. If the user has installed a root management tool such as SuperSU, the confirmation dialog will be popped up in the name of the 360 browser, which is likely to be trusted by users.
对于已经被root的手机:黑客可以随意对其做任何事,例如从后台网络安装APK安装包,获取邮件和短信,控制摄像头和耳机。事实上,它比“异次元之门”漏洞更加灵活。如果用户已经安装了例如SuperSU的root管理工具,伪装成360浏览器的确认对话框将会弹出,用户不会对其产生任何怀疑。
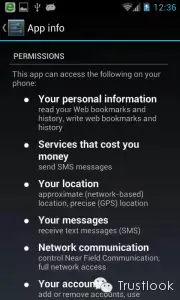
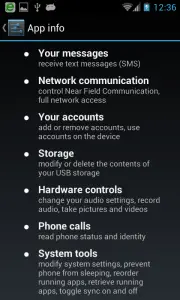
For unrooted phones: the attacker could share the permissions of the 360 browser, such as sending and accessing SMS, reading the call logs, accessing browser history, and monitoring the camera and microphone.
对于未被root的手机:黑客可以与360浏览器共享权限,例如发送和获取短信,浏览通话记录,获取历史浏览记录,控制摄像头和耳机。
As of today, Nov 23, most of the users have not upgraded their 360 browser to the latest version. The detailed analysis and exploitation code will be released in a later blog, after users have had a chance to protect themselves.
截至11月23日,大部分用户并未将360浏览器升级至最新版本。为了确保广大用户在第一时间得到保护,我们及时发布了这篇博客,详细的分析报告和被利用的代码将在后续的博客中发布。
We made a PoC video for this vulnerability. In this demo, we triggered it remotely on a rooted phone, and replaced the genuine banking app with an arbitrary app.
我们为这个漏洞录制了一段PoC视频。在这个演示中,我们在一个被root的手机上远程触发了这个漏洞,将手机中的正版银行应用更换为了任意一个其他应用。
Reference:
参考文献:
[1] http://www.wooyun.org/bugs/wooyun-2015-0155003
[2]头图来源网络