1-准备镜像
[root@VM-16-14-centos data]# mkdir -p controller-v1.0.4
[root@VM-16-14-centos data]# cd controller-v1.0.4/
[root@VM-16-14-centos controller-v1.0.4]# rz
rz waiting to receive.**B0100000023be50
[root@VM-16-14-centos controller-v1.0.4]# # Received /Users/shencaifeiyangdekk/Downloads/deploy.yml
[root@VM-16-14-centos controller-v1.0.4]# cp deploy.yml deploy.yml.bak
#修改镜像地址、取消多余的sha256值
[root@VM-16-14-centos controller-v1.0.4]# vim deploy.yml
[root@VM-16-14-centos controller-v1.0.4]# grep image deploy.yml
image: k8s.gcr.io/ingress-nginx/controller:v1.0.4
imagePullPolicy: IfNotPresent
image: k8s.gcr.io/ingress-nginx/kube-webhook-certgen:v1.1.1
imagePullPolicy: IfNotPresent
image: k8s.gcr.io/ingress-nginx/kube-webhook-certgen:v1.1.1
[root@VM-0-6-centos ~]# docker pull k8s.gcr.io/ingress-nginx/controller:v1.0.4
v1.0.4: Pulling from ingress-nginx/controller
Digest: sha256:545cff00370f28363dad31e3b59a94ba377854d3a11f18988f5f9e56841ef9ef
Status: Image is up to date for k8s.gcr.io/ingress-nginx/controller:v1.0.4
k8s.gcr.io/ingress-nginx/controller:v1.0.4
[root@VM-0-6-centos ~]# docker pull k8s.gcr.io/ingress-nginx/kube-webhook-certgen:v1.1.1
v1.1.1: Pulling from ingress-nginx/kube-webhook-certgen
Digest: sha256:64d8c73dca984af206adf9d6d7e46aa550362b1d7a01f3a0a91b20cc67868660
Status: Image is up to date for k8s.gcr.io/ingress-nginx/kube-webhook-certgen:v1.1.1
k8s.gcr.io/ingress-nginx/kube-webhook-certgen:v1.1.1
1.1-镜像导出与导入以及重命名tag
[root@VM-0-6-centos ~]# docker save c41e9fcadf5a -o /root/k8s.gcr.io_ingress-nginx_kube-webhook-certgen_v1.1.1.tar
[root@VM-0-6-centos ~]# docker save a9f76bcccfb5 -o /data/k8s.gcr.io_ingress-nginx_controller_v1.0.4.tar
[root@VM-0-6-centos data]# scp /data/k8s.gcr.io_ingress-nginx_* root@1.*.*.220:/data/
[root@VM-16-14-centos controller-v1.0.4]# docker load -i /data/k8s.gcr.io_ingress-nginx_controller_v1.0.4.tar
Loaded image ID: sha256:a9f76bcccfb5fdefff2c9e8c7cae3a6eb5a2593493370816640a40868115b300
[root@VM-16-14-centos controller-v1.0.4]# docker load -i /data/k8s.gcr.io_ingress-nginx_kube-webhook-certgen_v1.1.1.tar
Loaded image ID: sha256:c41e9fcadf5a291120de706b7dfa1af598b9f2ed5138b6dcb9f79a68aad0ef4c
[root@VM-16-14-centos controller-v1.0.4]#
[root@VM-16-14-centos controller-v1.0.4]#docker tag a9f76bcccfb5 k8s.gcr.io/ingress-nginx/controller:v1.0.4
[root@VM-16-14-centos controller-v1.0.4]#docker tag c41e9fcadf5a k8s.gcr.io/ingress-nginx/kube-webhook-certgen:v1.1.1
[root@VM-16-14-centos controller-v1.0.4]# cd /data/controller-v1.0.4
[root@VM-16-14-centos controller-v1.0.4]# kubectl apply -f deploy.yaml
1.2-报错
- 原因:之前指定了gcr.io k8s.gcr.io quay.io,导致无法解析。取消注释
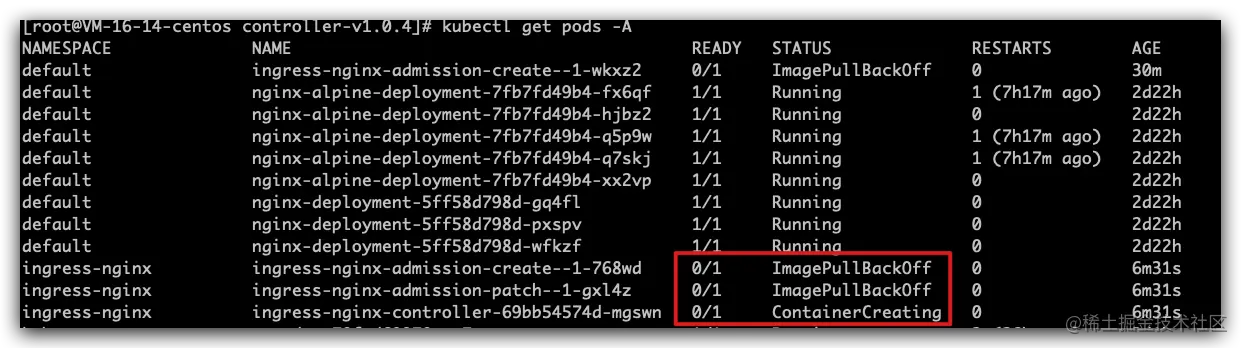
[root@VM-16-14-centos controller-v1.0.4]
[root@VM-16-14-centos controller-v1.0.4]
[root@VM-16-14-centos controller-v1.0.4]
2-部署
[root@VM-16-14-centos data]
rz waiting to receive.**B0100000023be50
[root@VM-16-14-centos data]
[root@VM-16-14-centos data]
v1: Pulling from koala2020/ingress-nginx-controller
540db60ca938: Already exists
f8a556c845c8: Pull complete
0844f14c29c0: Pull complete
332f89ee6ad4: Pull complete
2d40efc3f46e: Pull complete
df17be0b3f81: Pull complete
bbfc79e3b7aa: Pull complete
601d5801cae2: Pull complete
850129b50b3d: Pull complete
5fda179241d2: Pull complete
cadb7088686b: Pull complete
7929cf4b0068: Pull complete
ba8c8522b0ef: Pull complete
Digest: sha256:d7080bb71cc9c3a9d8b327a5d9b29edb0494ebcda4b4437f399c328db9883dff
Status: Downloaded newer image for koala2020/ingress-nginx-controller:v1
docker.io/koala2020/ingress-nginx-controller:v1
[root@VM-16-14-centos data]
v1: Pulling from koala2020/ingress-nginx-kube-webhook-certgen
0d7d70899875: Pull complete
ba6b482db037: Pull complete
Digest: sha256:a0f92f5f828e9bf8e3a4c672080067e0079e95f9af8583059eab0c11f4dc7cfe
Status: Downloaded newer image for koala2020/ingress-nginx-kube-webhook-certgen:v1
docker.io/koala2020/ingress-nginx-kube-webhook-certgen:v1
[root@VM-16-14-centos data]
[root@VM-16-14-centos data]
[root@VM-16-14-centos data]
image: koala2020/ingress-nginx-controller:v1
imagePullPolicy: IfNotPresent
image: koala2020/ingress-nginx-kube-webhook-certgen:v1
imagePullPolicy: IfNotPresent
image: koala2020/ingress-nginx-kube-webhook-certgen:v1
imagePullPolicy: IfNotPresent
[root@VM-16-14-centos data]
- ingress-nginx-controller达到running,大约需要120s
- ingress-nginx-admission,无视completed状态
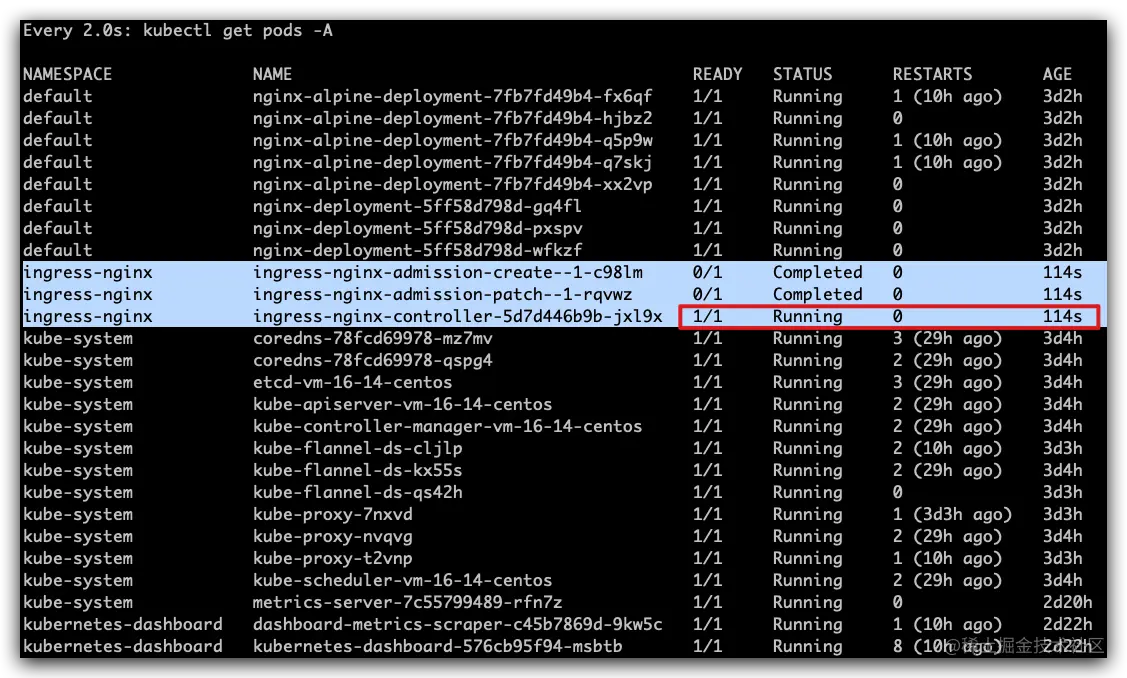
3-优化
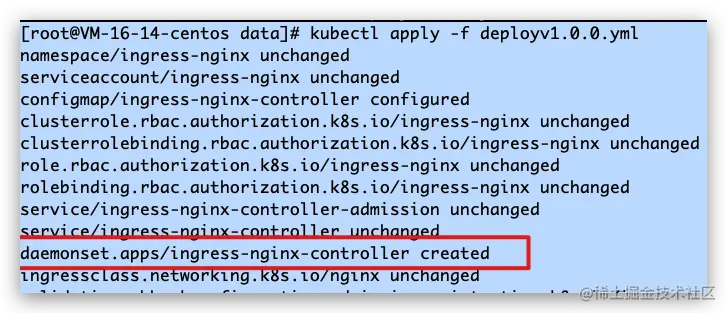
3.1-Deployment更改为DaemonSet
[root@VM-16-14-centos data]# kubectl apply -f deployv1.0.0.yml
- 各节点均有部署
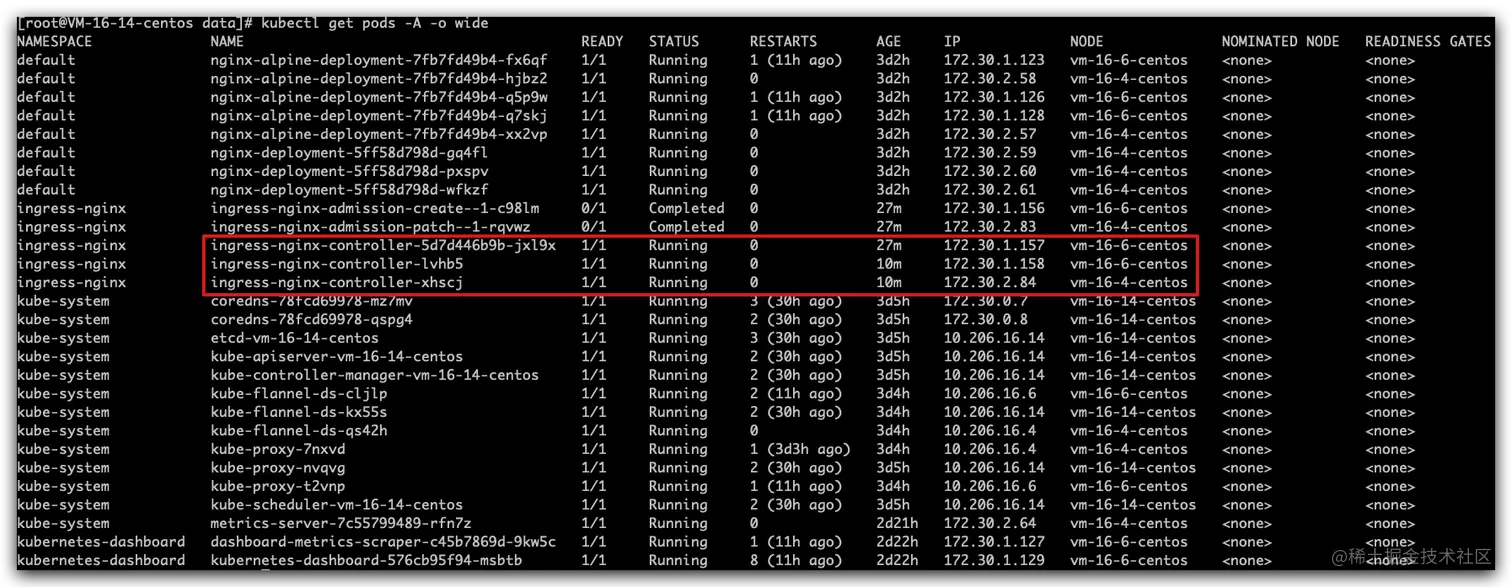
3.2-NodePort为固定端口
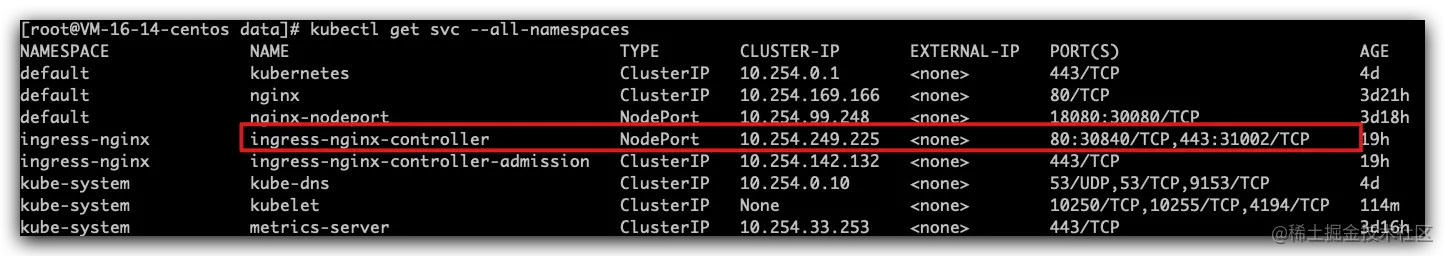
- 默认分配的NodePort为随机端口,如上 80:30840/TCP,443:31002/TCP
3.3-ingress默认命名空间
- 默认ingress使用default命名空间,如果不在该命名空间,会无法找到该svc,导致前台503
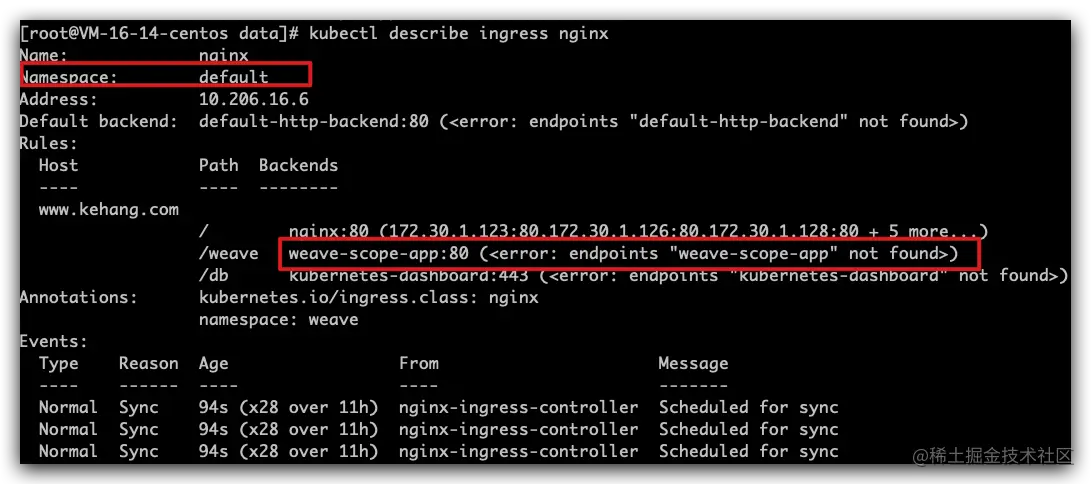
- 同时一个ingress文件只能指定一个namespace,所以需要拆分ingress文件为多个
- 本地写host文件,指向 node公网IP,通过80即可访问测试域名
在我的环境里,http://1.*.*.220:30840/ 访问404,31002 bad request