[译] 新 Cookie 安全模型即将到来,我们需要做哪些准备? (双语)
- 原文:Get Ready for New SameSite=None; Secure Cookie Settings
webmasters.googleblog.com/2020/01/get… - 译者:西楼听雨(微信名 t.t.)
- In May, Chrome announced a secure-by-default model for cookies, enabled by a new cookie classification system (spec). This initiative is part of our ongoing effort to improve privacy and security across the web.
- 在 5 月份的时候,Chrome 团队发布了一种默认安全的新 cookie 安全模型,该模型基于一种新的 cookie 分类系统,——我们一直致力于提升 Web 生态的隐私和安全,这个模型提案也是我们所做努力的一部分。
- Chrome plans to implement the new model with Chrome 80 in February 2020. Mozilla and Microsoft have also indicated intent to implement the new model in Firefox and Edge, on their own timelines. While the Chrome changes are still a few months away, It’s important that developers who manage cookies assess their readiness today. This blog post outlines high level concepts; please see SameSite Cookies Explained on web.dev for developer guidance.
- Chrome 计划在 2020 年 2 月份完成对这个新模型的实现。Mozilla 和微软也表示了会在他们自家的 Firefox 和 Edge 中实现这个新模型的意向。虽然距离 Chrome 完成新模型的实现还有几个月的时间,但提前了解新模型的就绪状态对开发人员来说也很重要。这篇博文就是针对此模型做高层次的概念介绍的,如果需要获取开发指南,请前往 web.dev 网站查看一篇名为 SameSite Cookies Explained (同站 Cookie 的解释)的文档。
Understanding Cross-Site and Same-Site Cookie Context
- 理解跨站 Cookie 环境和同站 Cookie 环境
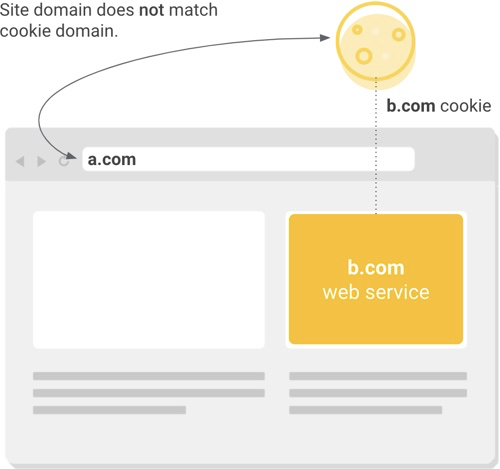
- Websites typically integrate external services for advertising, content recommendations, third party widgets, social embeds and other features. As you browse the web, these external services may store cookies in your browser and subsequently access those cookies to deliver personalized experiences or measure audience engagement. Every cookie has a domain associated with it. If the domain associated with a cookie matches an external service and not the website in the user’s address bar, this is considered a cross-site (or “third party”) context.
- 通常,网站都会嵌入一些外部服务,如广告、内容推荐、第三方小物件、社交媒体引用等。当你浏览网页时,这些外部服务可能会在你的浏览器中存储一些 cookie,然后后续再访问这些 cookie,以此提供个性化体验或测量受众的参与情况。每个 cookie 都归属与一个域名,如果某个 cookie 所归属的域名与用户地址栏中的网站不相符,这种情况就被视为 cross-site context(跨站点环境,又称“第三方”环境)。
- Less obvious cross-site use cases include situations where an entity that owns multiple websites uses a cookie across those properties. Although the same entity owns the cookie and the websites, this still counts as cross-site or “third party” context when the cookie’s domain does not match the site(s) from which the cookie is accessed.
- 有一类比较不明显的跨站场景:一个实体拥有多个网站,而这些网站都共用一个 cookie。虽然拥有这些网站和这个 cookie 的是同一个实体,但只要 cookie 的归属域名与这些网站域名不相符,就会遇到跨站环境或者“第三方”环境问题。
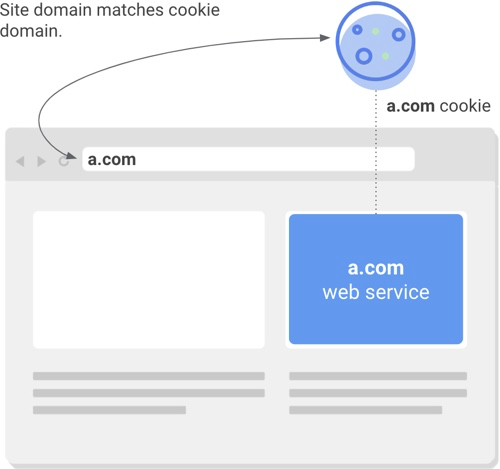
- In contrast, cookie access in a same-site (or “first party”) context occurs when a cookie’s domain matches the website domain in the user’s address bar. Same-site cookies are commonly used to keep people logged into individual websites, remember their preferences and support site analytics.
- 与跨站环境相反,当 cookie 的归属域名与用户地址栏中网站的域名相符合时,对 cookie 的访问就是发生在 same-site context(同站环境,又称“第一方环境”)中的。同站 cookie 通常用于记录人们在某个网站上的登陆状态、偏好,或者用于支持对网站的分析。
A New Model for Cookie Security and Transparency
- 一种新的 Cookie 安全和透明度模型
- Today, if a cookie is only intended to be accessed in a first party context, the developer has the option to apply one of two settings (SameSite=Lax or SameSite=Strict) to prevent external access. However, very few developers follow this recommended practice, leaving a large number of same-site cookies needlessly exposed to threats such as Cross-Site Request Forgery attacks.
- 目前,对于某个 cookie,如果只打算在第一方环境中使用的话,开发人员可以对其采用两种设置来防止外部访问,一种是 SameSite=Lax,一种是 SameSite=Strict。然而,很少有开发人员遵从这条实践建议,任由大量的同站 cookie 暴露在隐患(如跨站请求伪造攻击)之下。
- To safeguard more websites and their users, the new secure-by-default model assumes all cookies should be protected from external access unless otherwise specified. Developers must use a new cookie setting, SameSite=None, to designate cookies for cross-site access. When the SameSite=None attribute is present, an additional Secure attribute must be used so cross-site cookies can only be accessed over HTTPS connections. This won’t mitigate all risks associated with cross-site access but it will provide protection against network attacks.
- 为了将更多的网站和他们的用户纳入保护,除非作出明确指定,新的模型将假设所有 cookie 都默认不能外部访问。开发人员必须采用新的 cookie 设置: SameSite=None,以此来标识 cookie 支持跨站访问。如果希望其只能在 HTTPS 连接下被访问,除了指定了 SameSite=None 属性,还必须另外设置一个属性: Secure。
- Beyond the immediate security benefits, the explicit declaration of cross-site cookies enables greater transparency and user choice. For example, browsers could offer users fine-grained controls to manage cookies that are only accessed by a single site separately from cookies accessed across multiple sites.
- 除了上述明显的安全提升外,显式声明 cookie 支持跨站,还可以让安全性变得更加透明,用户也多了更多的选择。例如,浏览器可以借此给用户提供更精细化的 cookie 管理,让用户可以对跨站 cookie 和同站 cookie 进行单独管理。
Chrome Enforcement Starting in February 2020
- Chrome 将在 2020 年 2 月开始启用新模型
- With Chrome 80 in February, Chrome will treat cookies that have no declared SameSite value as SameSite=Lax cookies. Only cookies with the SameSite=None; Secure setting will be available for external access, provided they are being accessed from secure connections. The Chrome Platform Status trackers for SameSite=None and Secure will continue to be updated with the latest launch information.
- 随着 Chrome 80 在 2月发布,届时,Chrome 会把没有明确指定 SameSite 属性值的 cookie 视为 SameSite=Lax;且只有 SameSite=None; Secure 的 cookie 才支持安全连接(即 HTTPS)下的外部访问。
- Mozilla has affirmed their support of the new cookie classification model with their intent to implement the SameSite=None; Secure requirements for cross-site cookies in Firefox. Microsoft recently announced plans to begin implementing the model starting as an experiment in Microsoft Edge 80.
- Mozilla 已经证实了将在 Firefox 中支持新的 cookie 分类模型以及跨站 cookie 需要设置SameSite=None; Secure 的要求。微软也在最近宣称,计划在 Edge 80 以试验性选项对新模型进行实现。
How to Prepare; Known Complexities
- 需要提前做的准备以及已知的一些问题
- If you manage cross-site cookies, you will need to apply the SameSite=None; Secure setting to those cookies. Implementation should be straightforward for most developers, but we strongly encourage you to begin testing now to identify complexities and special cases, such as the following:
- 如果你管理着跨站 cookie,你需要把这些 cookie 设置成SameSite=None; Secure。对于开发人员来说,实现起来可能比较简单,很快就完成了,但我们强烈建议从现在开始就对其进行测试,以此提前暴露其复杂性和边缘场景,例如:
- Not all languages and libraries support the None value yet, requiring developers to set the cookie header directly. This Github repository provides instructions for implementing SameSite=None; Secure in a variety of languages, libraries and frameworks.
- 不是所有语言和库都支持 None 值设置,所以需要开发人员直接设置 Cookie 头。这里有个 Github 仓库提供了在各种语言、库、框架中设置 Same=Site=None; Secure 的方法。
- Some browsers, including some versions of Chrome, Safari and UC Browser, might handle the None value in unintended ways, requiring developers to code exceptions for those clients. This includes Android WebViews powered by older versions of Chrome. Here’s a list of known incompatible clients.
- 有些浏览器——包括某些版本的 Chrome、Safari、UC——可能不会以预想的方式处理 None 值,所以需要开发人员对这些浏览器客户端进行异常处理。这里有一个已证实不兼容的浏览器客户端清单。
- App developers are advised to declare the appropriate SameSite cookie settings for Android WebViews based on versions of Chrome that are compatible with the None value, both for cookies accessed via HTTP(S) headers and via Android WebView's CookieManager API, although the new model will not be enforced on Android WebView until later.
- 建议 App 开发人员在设置 SameSite 时,
- Enterprise IT administrators may need to implement special policies to temporarily revert Chrome Browser to legacy behavior if some services such as single sign-on or internal applications are not ready for the February launch.
- 如果在 2 月份 Chrome 发布的时候,企业里的某些服务如单点登陆或者内部应用还没有完成调整,那么企业的 IT 管理人员可能需要制定一些特殊的策略,以此临时性地将 Chrome 浏览器回退到老版本。
- If you have cookies that you access in both a first and third-party context, you might consider using separate cookies to get the security benefits of SameSite=Lax in the first-party context.
- 如果有些 cookie 在第一方环境和第三方环境下都会用到,那么你可以考虑将其拆开,在第一方环境中使用 SameSite=Lax。
- To test the effect of the new Chrome behavior on your site or cookies you manage, you can go to chrome://flags in Chrome 76+ and enable the “SameSite by default cookies” and “Cookies without SameSite must be secure” experiments. In addition, these experiments will be automatically enabled for a subset of Chrome 79 Beta users. Some Beta users with the experiments enabled could experience incompatibility issues with services that do not yet support the new model; users can opt out of the Beta experiments by going to chrome://flags and disabling them.
- 如果你想对即将到来的新版 Chrome 可能对你的网站和 cookie 造成的影响做测试,你可以在 76 版本以上的 Chrome 中打开 chrome://flags 这个地址,并启用其中的 “SameSite by default cookies” 、 “Cookies without SameSite must be secure” 这两个试验性选项。另外需要注意的是,Chrome 79 Beta 版本的一部分用户是默认开启了这两个选项的,而有些服务还未支持这个新模型,所以有些 Beta 版本的用户可能会碰到兼容性问题,如果有需要,可以把这两个选项禁用掉。
- 译注:
- 1. 开启 “SameSite by default cookies” 选项后,没有设置 SameSite 属性的 cookie,会被视为 SameSite=Lax。
- 2. 开启“Cookies without SameSite must be secure”选项后,设置了 SameSite=None 的 cookie,还必须设置 Secure 才能跨站访问。
- If you manage cookies that are only accessed in a same-site context (same-site cookies) there is no required action on your part; Chrome will automatically prevent those cookies from being accessed by external entities, even if the SameSite attribute is missing or no value is set. However we strongly recommend you apply an appropriate SameSite value (Lax or Strict) and not rely on default browser behavior since not all browsers protect same-site cookies by default.
- 如果你只管理着同站环境的 cookie,那么你可以不作出任何变动,Chrome 会自动帮你阻止外部实体访问这些 cookie——即便你没有设置 SameSite 属性或者没有给这个属性赋值。不过我们还是建议你把 SameSite 属性值(Lax/Strict)给赋上,不要依赖于浏览器的默认行为,因为不是所有浏览器默认都会保护你的“同站 cookie”。
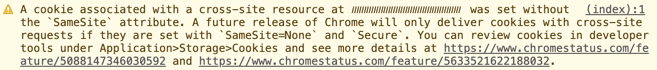
- Finally, if you’re concerned about the readiness of vendors and others who provide services to your website, you can check for Developer Tools console warnings in Chrome 77+ when a page contains cross-site cookies that are missing the required settings:
- 最后,如果你比较关心浏览器厂商们以及给你网站提供提供第三方服务的提供商们的就绪状态,你可以打开 Chrome 77 以上版本的开发者工具,看看是不是有控制台警告——如果页面包含跨站 cookie,且该 cookie 没有相关的设置时,就会发出警告:
- Some providers (including some Google services) will implement the necessary changes in the months leading up to Chrome 80 in February; you may wish to reach out to your partners to confirm their readiness.
- 某些服务提供方(包括 Google 的某些服务)会在 2 月份 Chrome 80 发布前的这几个月里作出相应的调整;不过关于你合作伙伴们的就绪情况,你可能要跟他们确认下。
- 关于本文
- 本文同时发布与于
- 打赏:你的一枚硬币,造就的却可能是下一代比尔·盖茨
- 联系 & 交流 & 聘用